Up to 1 Million email Accounts Phished for Identity Theft
Robert Siciliano Identity Theft Expert
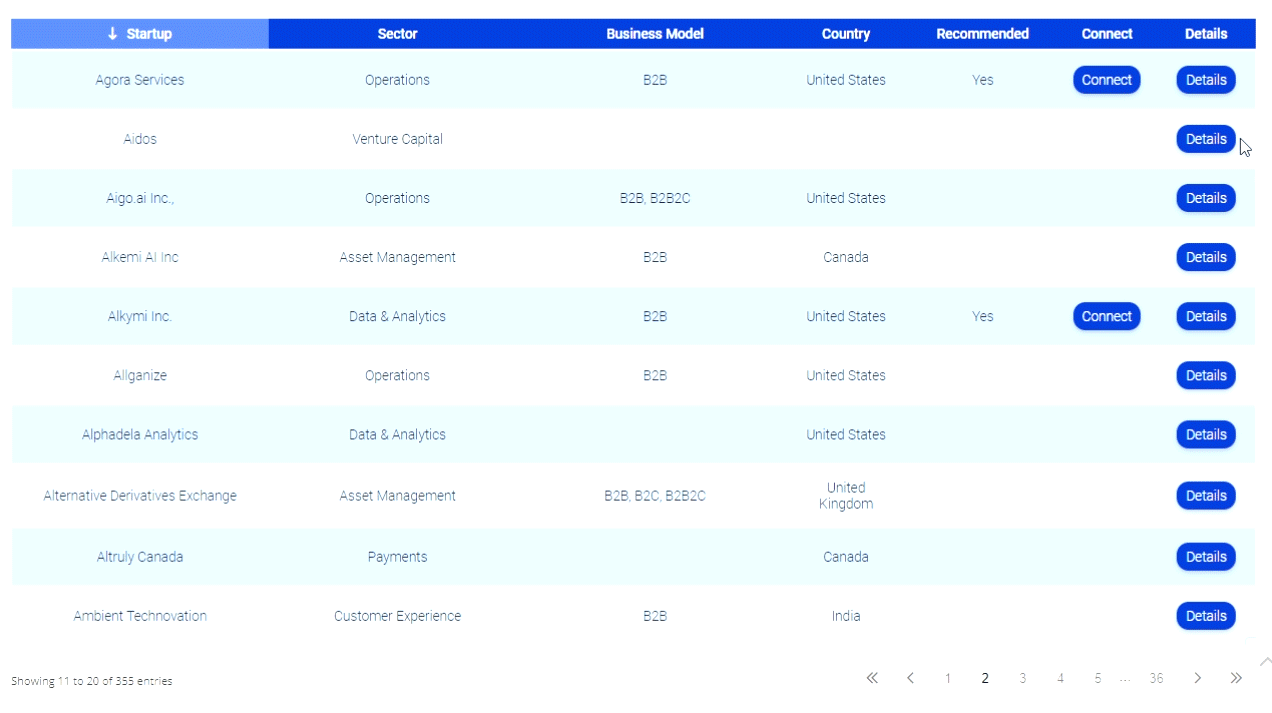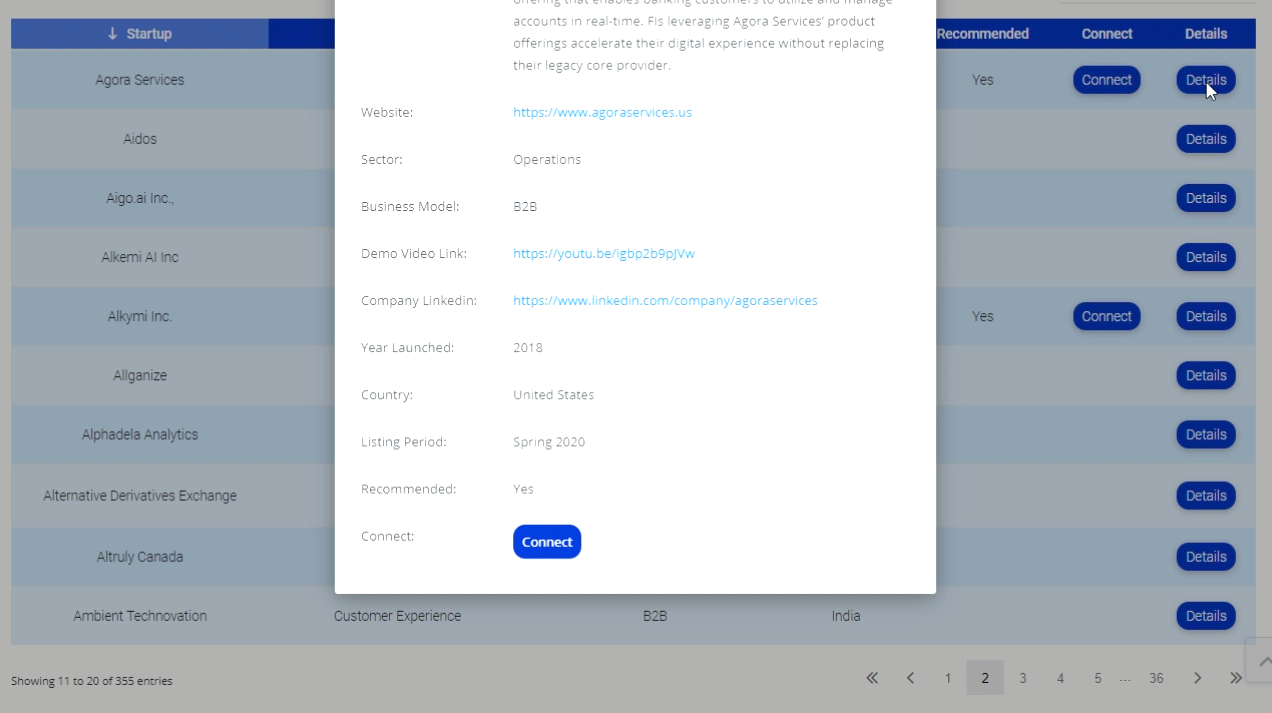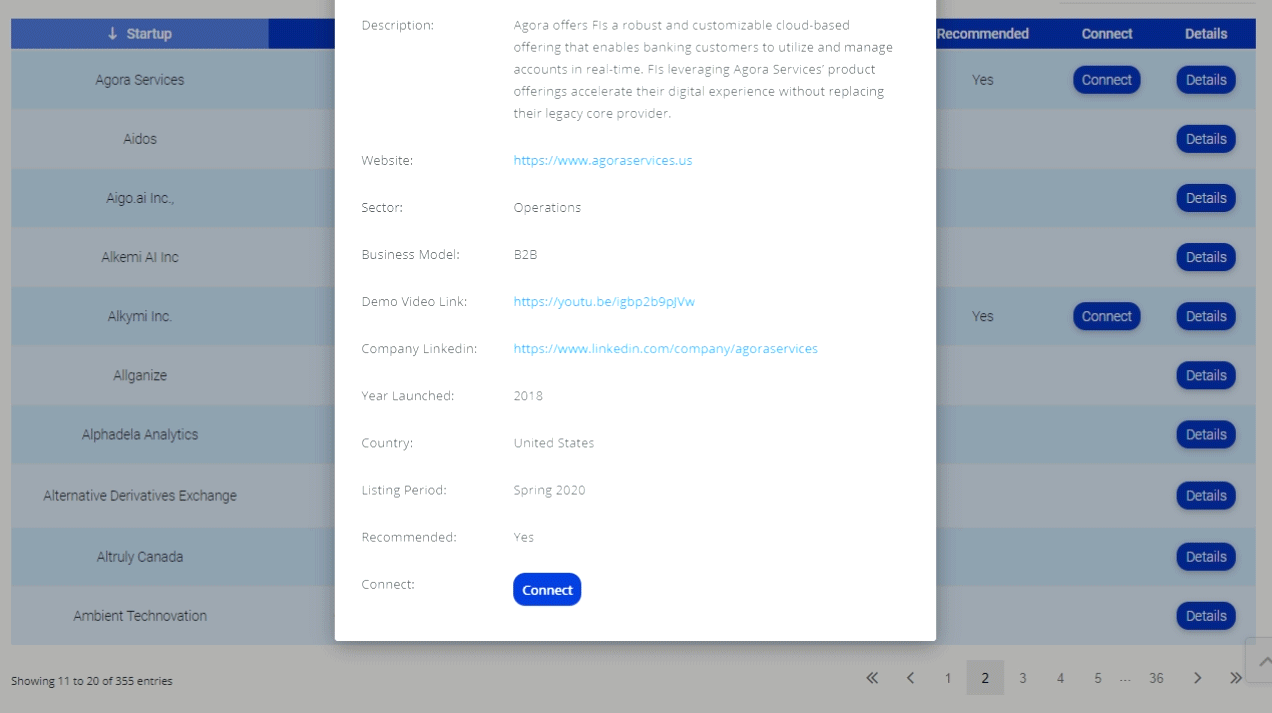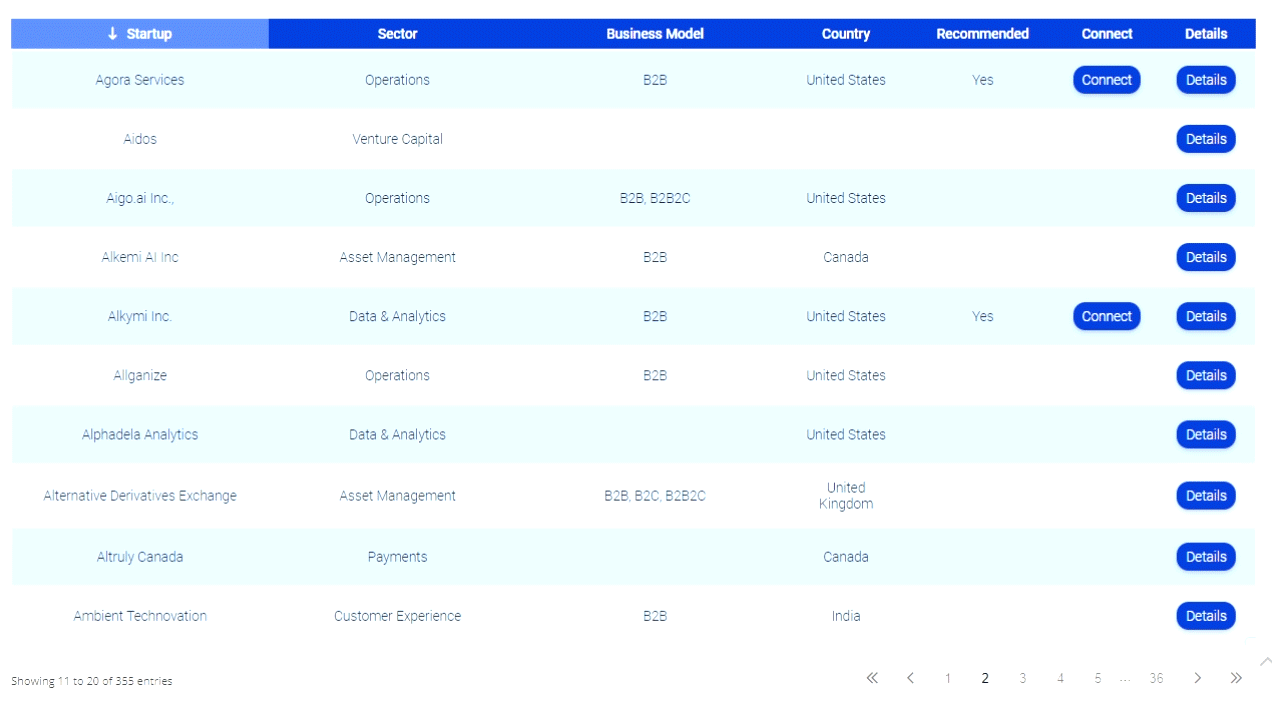
Hotmail, Earthlink, Google, Yahoo, Comcast and other web-based email users have been giving up al their login details to phishers and current estimates are as many as 1 million accounts may have been compromised.
News of the scam broke when technology blog neowin.net reported an anonymous user had published confidential details on pastebin.com. Internet users are urged to change their passwords regularly and ensure anti-virus software is up to date to protect themselves from fraudsters.
While phishing emails keep pouring in, their methods are changing rapidly. Posing as a Nigerian prince is still common, but not as effective. Even posing as a known bank or Paypal, asking to update an account for various reasons and requesting a potential victim’s user name and password is not as effective as it used to be.
Much of the phishing that occurs today is targeted “spear phishing,” in which the spammers are after a localized target. Going after a CEO is called “whaling.” Who better to take down than the biggest phish of them all? Most corporate websites offer plenty of data on the company officers and administrative contacts, which makes it relatively easy to create a sucker list. If scammers send an email blast to the entire company, eventually someone is likely to cough up enough data to allow the scammers to tap into the company’s intranet. Once the scammers have accessed the intranet, all further phishing emails will appear to be coming from a trusted, internal source.
Perhaps the most insidious type of phishing occurs when a recipient clicks a link, either in the body of an email or on the spoofed website linked in the email, and a download begins. That download is almost always a virus with a remote control component , which gives the phisher full access to the user’s data, including usernames and passwords, credit cards details, banking and Social Security numbers. Often, that same virus makes the victim’s PC part of a botnet.
How to avoid becoming a victim? Delete.
Change passwords often. Combine uppercase and lowercase letters, as well as numbers and characters. Don’t use consecutive letters or numbers, and never use names of pets, family members, or close friends. Instead use the first letters of phrases
Never click links in the body of an email that are coming from a bank, Paypal or any enterprise that may be leading to a request to enter data. Go to your favorites menu or manually type the address in.
Pay attention to phishing filters. Most updated browsers have built-in phish filters that toss up a red flag warning of a potential ruse.
1. Protecting yourself from new account fraud requires effort. You can attempt to protect your own identity, by getting yourself a credit freeze, or setting up your own fraud alerts. There are pros and cons to each.
2. Invest in Intelius Identity Protection and Prevention. Because when all else fails you’ll have someone watching your back.
Robert Siciliano, identity theft speaker, discusses hacked email on FOX & Friends.
Robert Siciliano Identity Theft Expert
Hotmail, Earthlink, Google, Yahoo, Comcast and other web-based email users have been giving up al their login details to phishers and current estimates are as many as 1 million accounts may have been compromised.
News of the scam broke when technology blog neowin.net reported an anonymous user had published confidential details on pastebin.com. Internet users are urged to change their passwords regularly and ensure anti-virus software is up to date to protect themselves from fraudsters.
While phishing emails keep pouring in, their methods are changing rapidly. Posing as a Nigerian prince is still common, but not as effective. Even posing as a known bank or Paypal, asking to update an account for various reasons and requesting a potential victim’s user name and password is not as effective as it used to be.
Much of the phishing that occurs today is targeted “spear phishing,” in which the spammers are after a localized target. Going after a CEO is called “whaling.” Who better to take down than the biggest phish of them all? Most corporate websites offer plenty of data on the company officers and administrative contacts, which makes it relatively easy to create a sucker list. If scammers send an email blast to the entire company, eventually someone is likely to cough up enough data to allow the scammers to tap into the company’s intranet. Once the scammers have accessed the intranet, all further phishing emails will appear to be coming from a trusted, internal source.
Perhaps the most insidious type of phishing occurs when a recipient clicks a link, either in the body of an email or on the spoofed website linked in the email, and a download begins. That download is almost always a virus with a remote control component , which gives the phisher full access to the user’s data, including usernames and passwords, credit cards details, banking and Social Security numbers. Often, that same virus makes the victim’s PC part of a botnet.
How to avoid becoming a victim? Delete.
Change passwords often. Combine uppercase and lowercase letters, as well as numbers and characters. Don’t use consecutive letters or numbers, and never use names of pets, family members, or close friends. Instead use the first letters of phrases
Never click links in the body of an email that are coming from a bank, Paypal or any enterprise that may be leading to a request to enter data. Go to your favorites menu or manually type the address in.
Pay attention to phishing filters. Most updated browsers have built-in phish filters that toss up a red flag warning of a potential ruse.
1. Protecting yourself from new account fraud requires effort. You can attempt to protect your own identity, by getting yourself a credit freeze, or setting up your own fraud alerts. There are pros and cons to each.
2. Invest in Intelius Identity Protection and Prevention. Because when all else fails you’ll have someone watching your back.
Robert Siciliano, identity theft speaker, discusses hacked email on FOX & Friends.