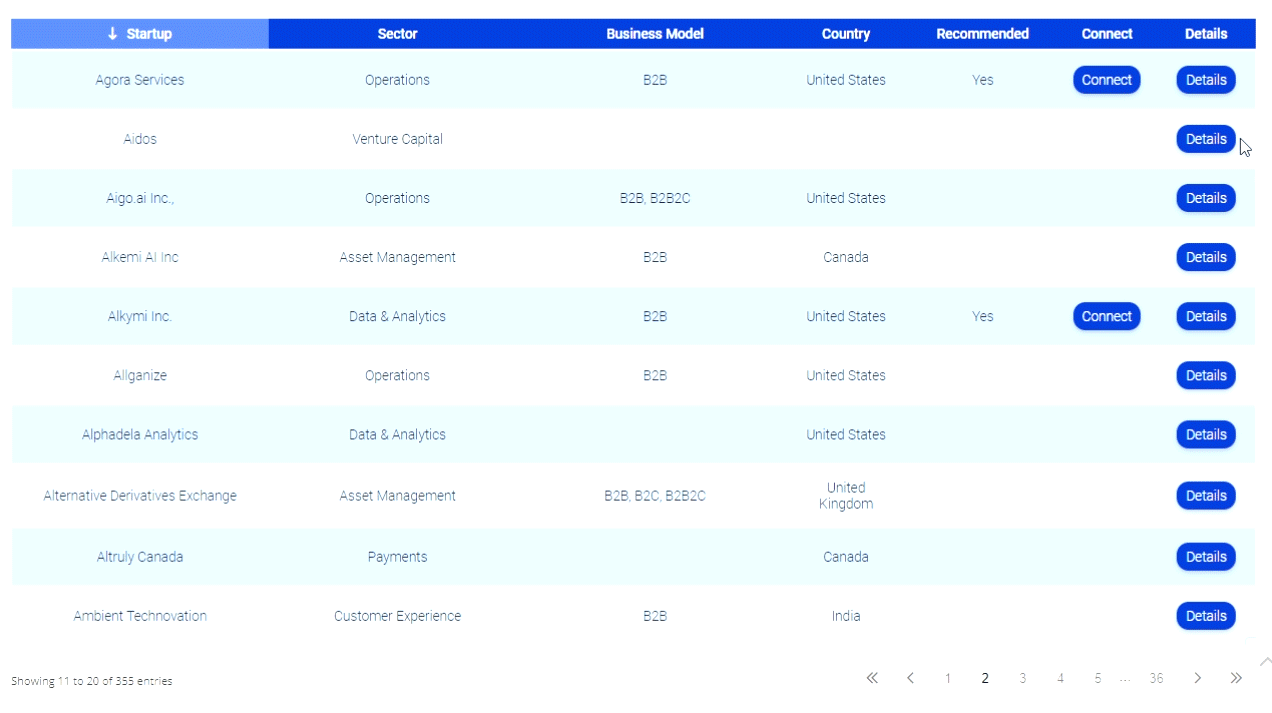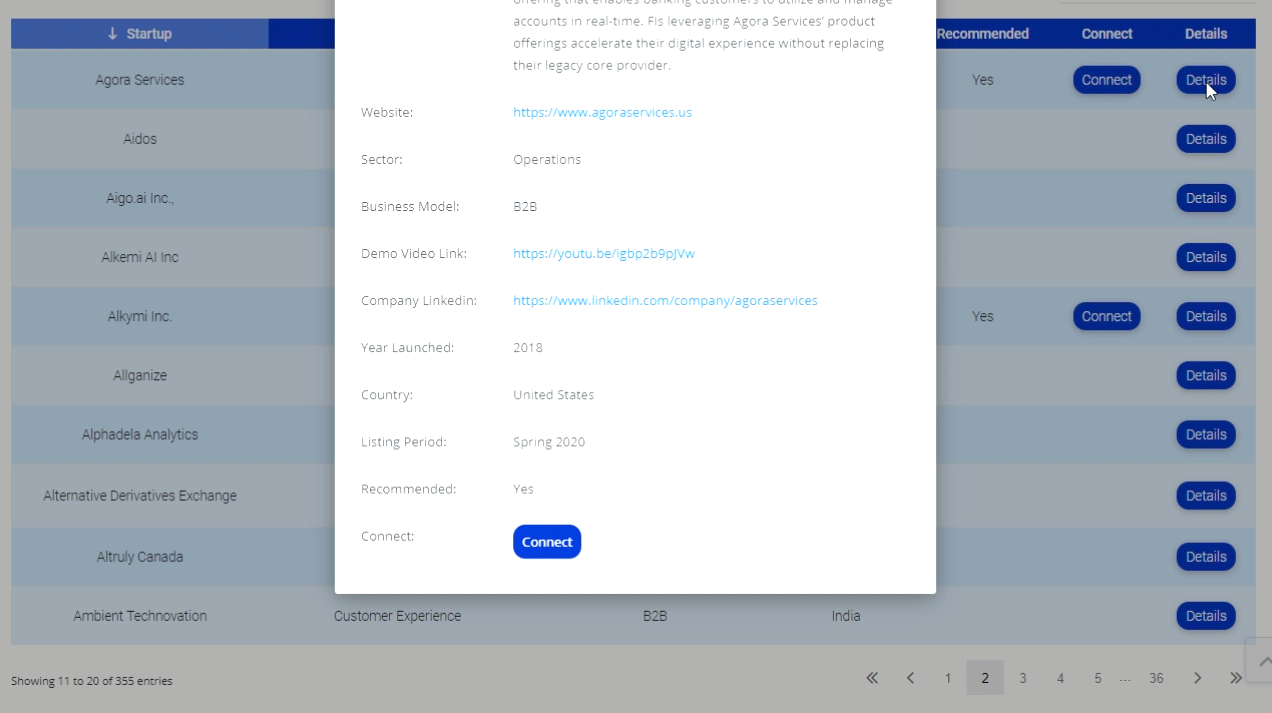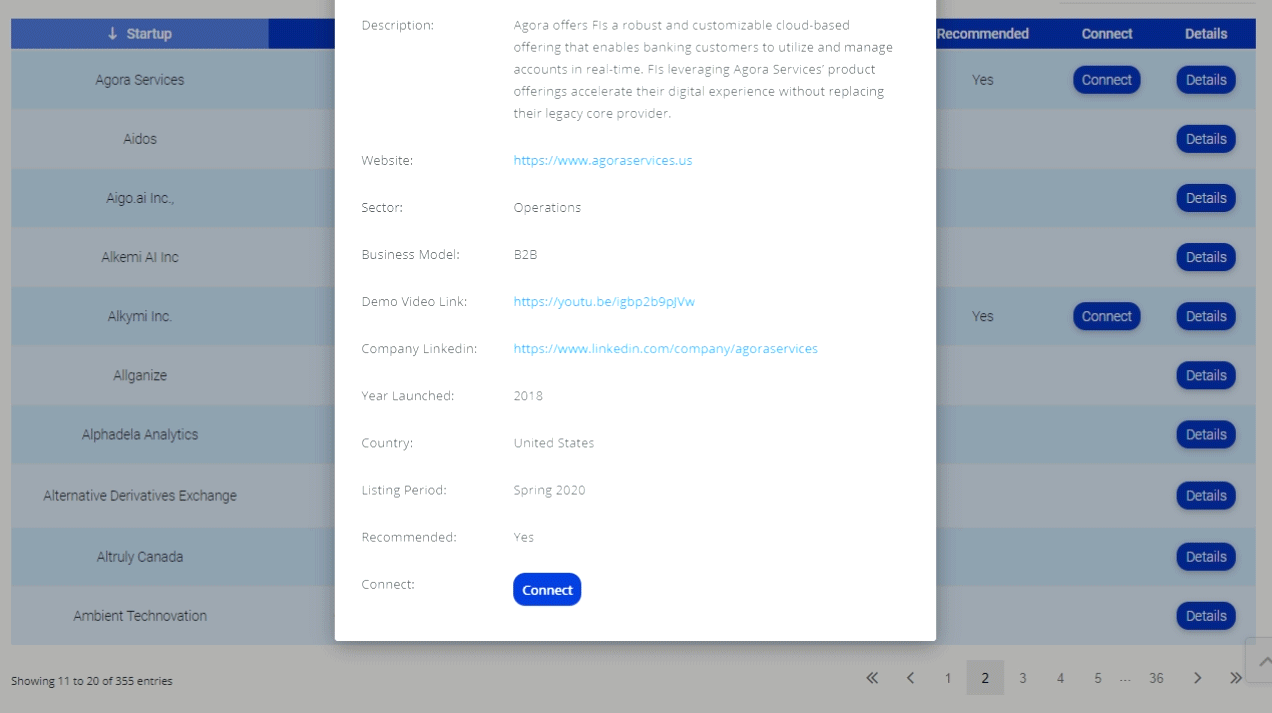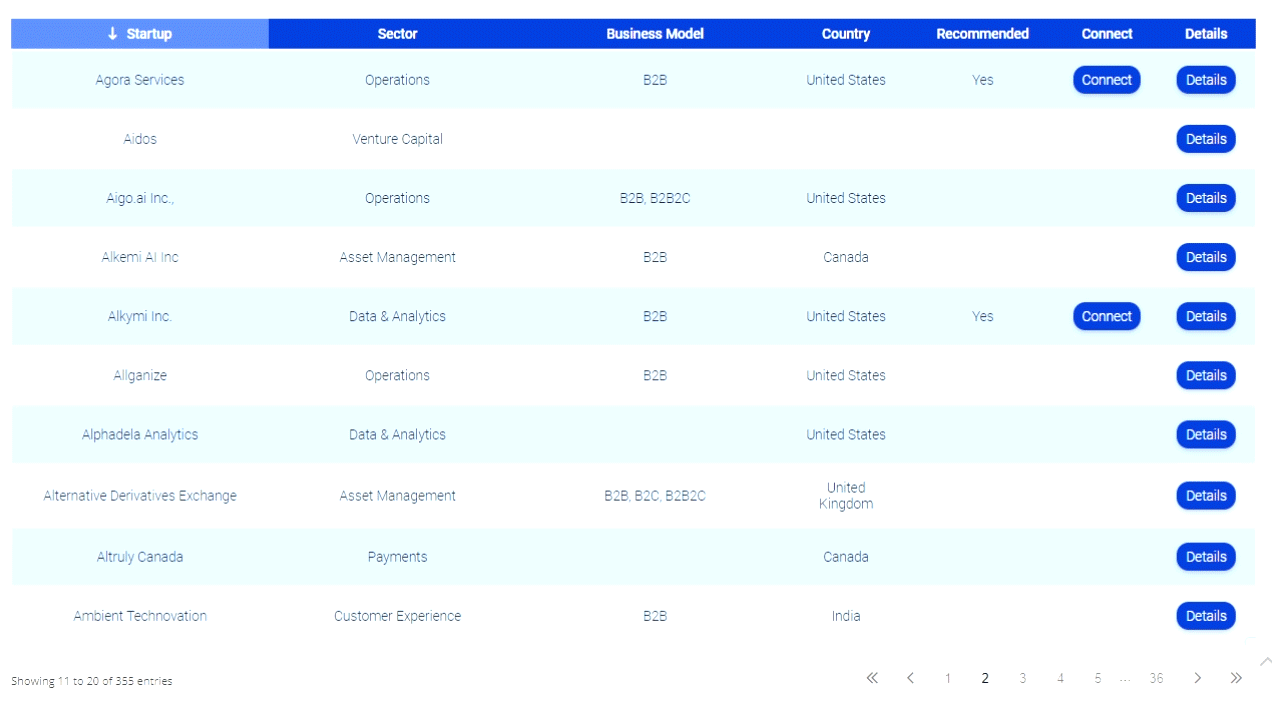
How Will Banks Secure the New Channels — Messaging, Video, Chatbots?

There are more ways for customers to talk to banks than ever — and therefore, more avenues for fraud to travel. How will banks secure these channels?
“Any communication channel will see criminals,” David Pollino, deputy chief security officer at Bank of the West told Bank Innovation. “So you need to have a policy as to what level of security will be present.”
Certain channels that are quite popular for customer engagement, such as Twitter or Facebook, are particularly problematic. Banks must occupy these spaces, or surrender them to impostors that could damage the brand, Pollino said. So while the channel remains open for conversations, authenticating users there is another matter. “We have reached the conclusion that you cannot perform authentication over social media,” Pollino said. “You may be verified on Twitter but the bank hasn’t verified you.”
A bank in Greece authenticates customers over Skype with challenge questions. “Skype and FaceTime were not built to be secure channels,” said Gene Pranger, CEO of the communication technology company Financial Town, the company that claims to have made the first transatl banking video call. “Financial services companies, and any discussion of a complex product requires a controlled environment to meet regulatory hurdles.” Financial Town offers a variety of authentication schemes, from PINs to biometrics, to meet these requirements.
Mary Ann Miller, senior director at NICE Actimize, said that banks need to bring in as many data points as possible when authenticating customers and approving transactions in new channels.
“If the customer is applying for a product, or changing account information, or making a payment, on a mobile device, all of these events need to be managed in relation to each other,” Miller said. “That kind of environment is new.”
If a customer attempts to log in using biometrics and fails, for example, “you don’t just want to slam the door,” Miller said. “You want to be able to guide them to what to do next. You look at the data being collected and direct customers to the next event.” Miller referred to this as “continuous authentication.”
“What I’m seeing is failure to authenticate is causing customers to re-enroll or get dropped out of sessions, and that doesn’t need to be the case,” Miller said. Banks can leverage the passive data — device information, location, etc. — to determine whether it’s their customer or not. “You escalate them to another environment,” Miller said, noting this may mean moving a customer out of a preferred channel. “Then you decide what you’ll allow them to do in that environment.”
The key may be not annoying the customer. “Customers want you to say ‘Yes’ when it’s them and ‘No’ when it’s not them,” Pollino said.