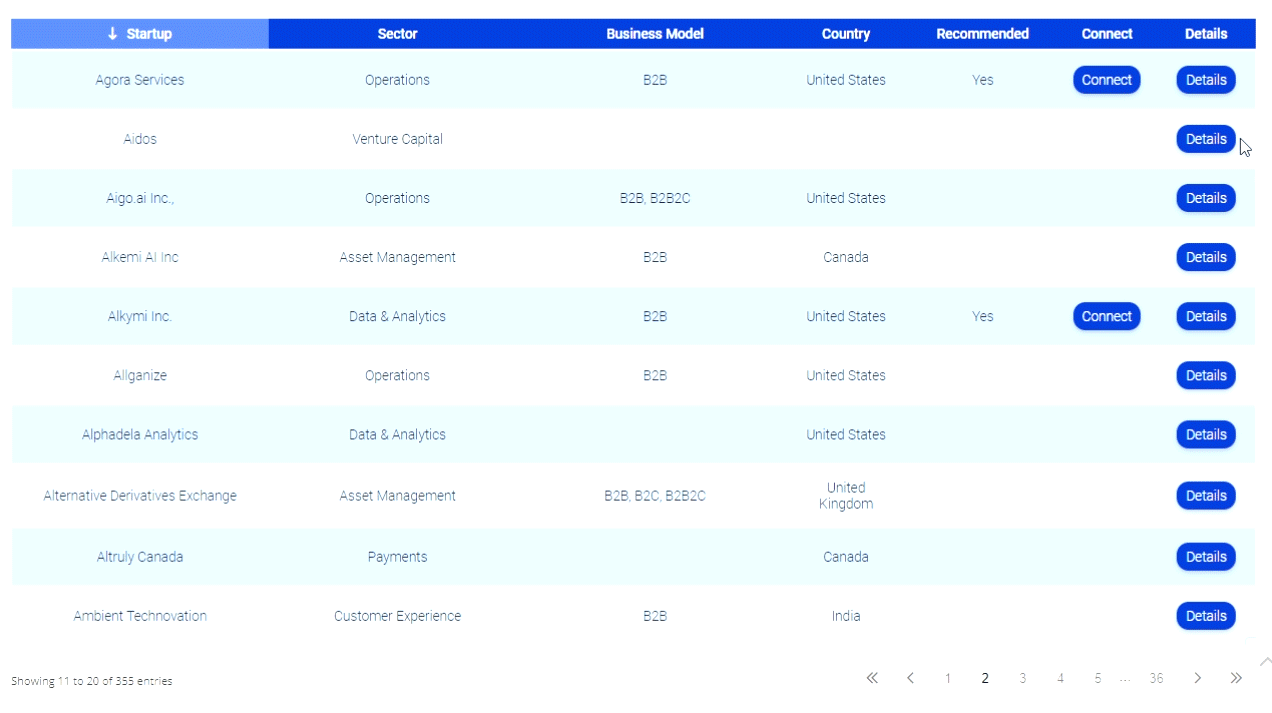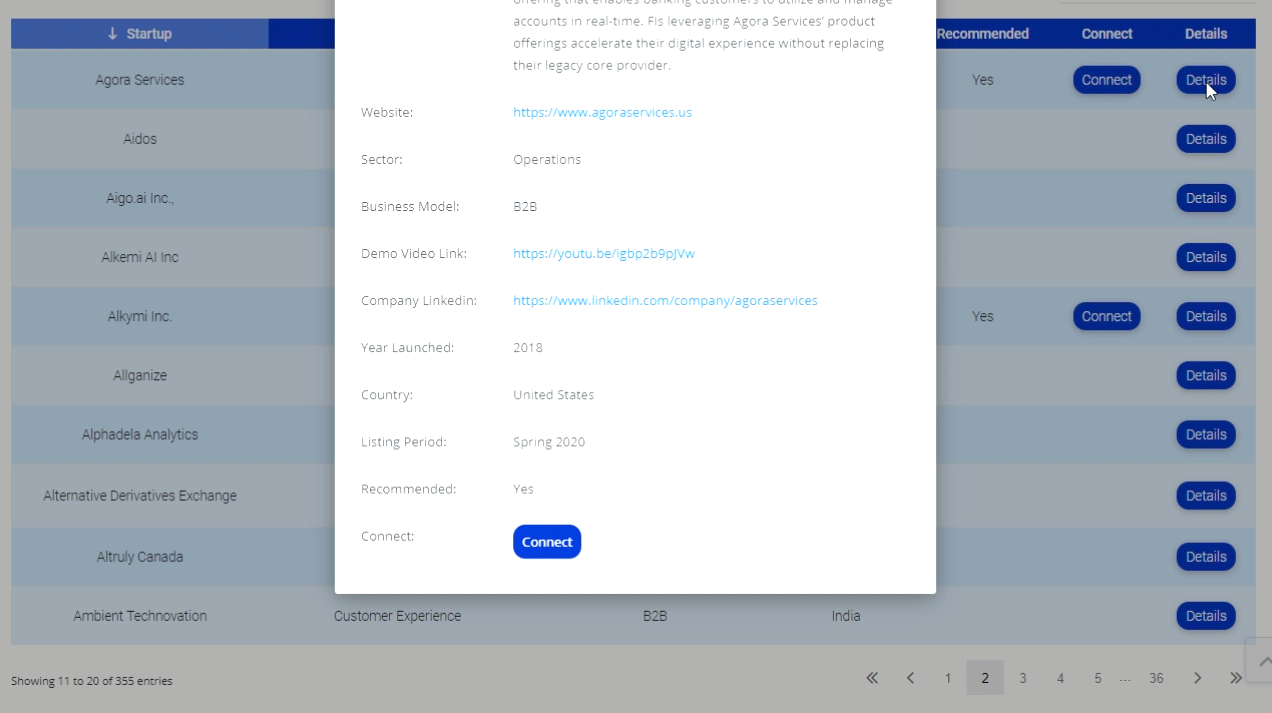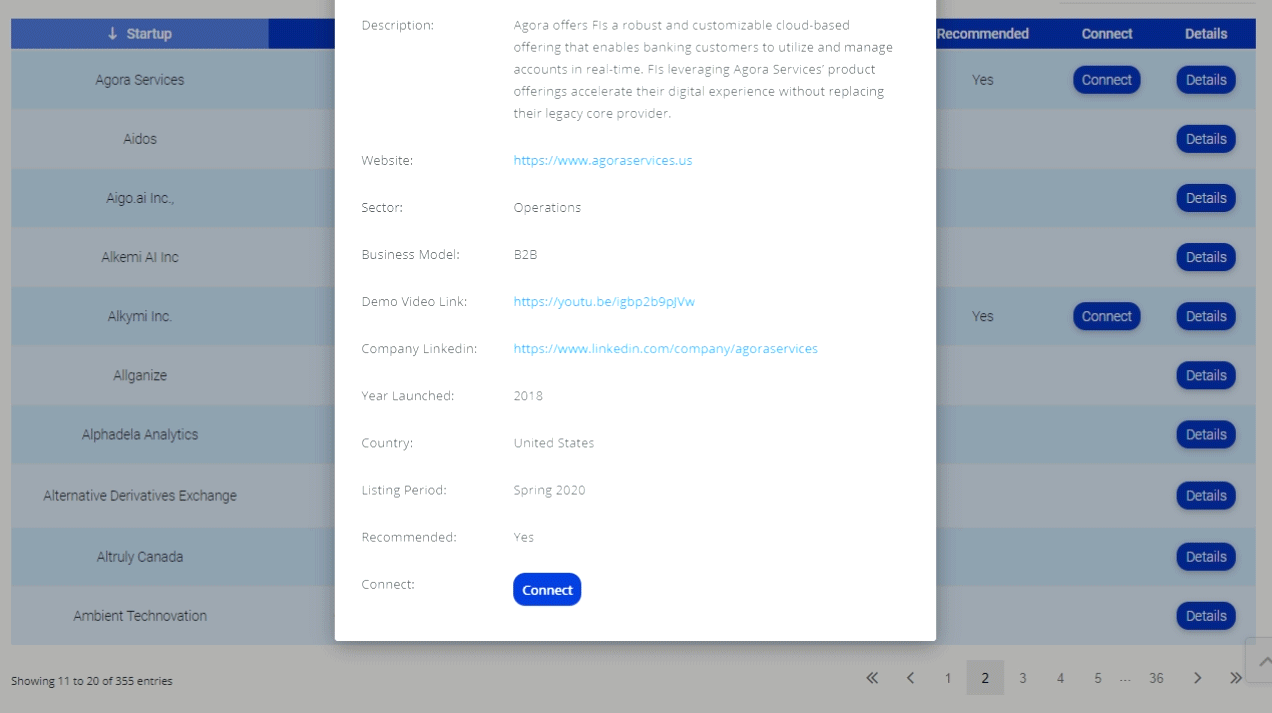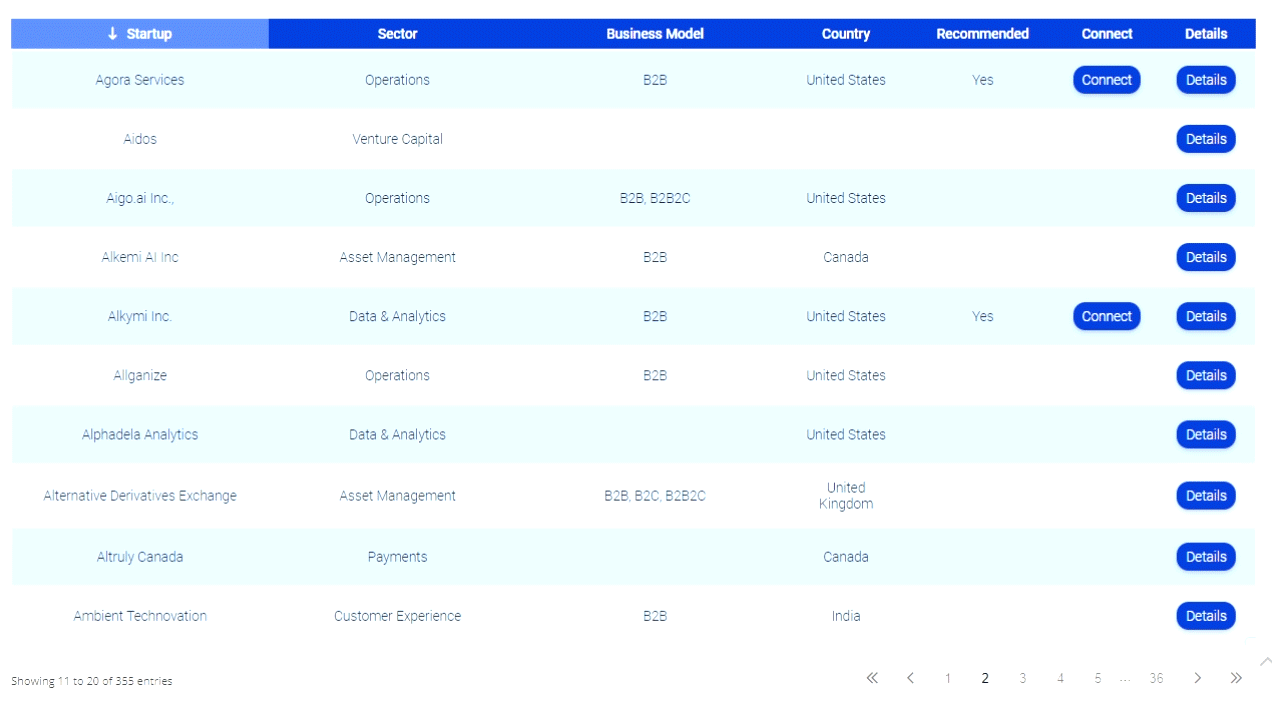
Social Media Identity Theft Hits Baseball Coach On Twitter
Identity Theft Expert Robert Siciliano
The scourge of identity theft knows no boundaries. It can happen to anyone: rich, poor, good credit, bad credit. Victims include children, the elderly, celebrities and politicians, even the dead. Identity theft may include new account fraud, account takeover, criminal identity theft, business identity theft and medical identity theft. Most of these result in financial loss.
One form of identity theft that is particularly damaging to the victim’s reputation is social media identity theft. Social media identity thieves have various motivations. The most damaging type of social media identity theft occurs when someone poses as you in order to disrupt your life. This disruption can take on many forms. They may harass and stalk you or your contacts, or they may steal your online identity for financial gain.
In the case of St. Louis Cardinals manager Tony La Russa, someone created a Twitter account in his name. La Russa is suing Twitter, claiming the impostor Twitter page damaged his reputation and caused emotional distress. The lawsuit includes a screen shot of three tweets. One, posted on April 19, read, “Lost 2 out of 3, but we made it out of Chicago without one drunk driving incident or dead pitcher.” Apparently, La Russa has had a drunk driving arrest and two Cardinals pitchers have died since 2002. One pitcher died of a heart attack, the other in a drunk driving accident.
There is no limit to the damage someone can do by using your name and picture in order to impersonate you online. In Milwaukee, Wisconsin, an 18 year old student was accused of posing as a girl on Facebook, tricking at least 31 male classmates into sending him naked photos of themselves, and then blackmailing some of these young men for sex acts.
Social media websites were created with the intention of bringing people together in a positive way, but we are beginning to see these sites being used in very sinister ways. The root of the problem is the fact that social media sites are all based on the honor system, with the assumption that people are honestly setting up accounts in their own names. There are few checks and balances in the world of social media, which means that you need to adopt a strategy from yet another form of predator to protect yourself.
There are hundreds or even thousands of social media sites, including Facebook, MySpace, Twitter and YouTube. Even your local newspaper’s website has a place for user comments, and most people would prefer to register their own names before someone else has done so on their behalf.
I have obtained over 200 user names pertaining to my given name in order to mitigate social media identity theft. This may sound obsessive, but the two examples given above are all the proof anyone needs to clamp down on social media. I’m on everything from Affluence.org to Zooomr.com. Some I use, others just have my profile and a link back to my website. I should also mention that there are some hazards involved in such a mission. You may experience a spike in spam, as I did, so I suggest creating an alternate email address. Furthermore, some websites make you join various groups that you don’t have much control over. I’m now a member of some masochistic fetish group of the opposite sex. Not exactly what I signed up for. So be careful.
The goal is to obtain your real first and last name without periods, underscores, hyphens, abbreviations or extra numbers or letters.
- Register your full name and those of your spouse and kids on the most trafficked social media sites, blogs, domains or web based email accounts. If your name is already gone, include your middle initial, a period or a hyphen. It’s up to you to decide whether or not to plug in your picture and basic bio, but consider leaving out your age or birthday.
- Set up a free Google Alerts for your name and get an email every time your name pops up online.
- Set up a free StepRep account for your name. StepRep is an online reputation manager that does a better job than Google Alerts does of fetching your name on the web.
- Consider dropping $65 on Knowem.com. This is an online portal that goes out and registers your name at what they consider the top 120 social media sites. Their top 120 is debatable, but a great start. The user experience with Knowem is relatively painless. There is still labor involved in setting things up and with some of the 120. And no matter what you do, you will still find it difficult to complete the registration with all 120 sites. Some of the social media sites just aren’t agreeable. This can save you lots of time, but is only one part of solving the social media identity theft problem.
- Start doing things online to boost your online reputation. Blogging is best. You want Google to bring your given name to the top of search in its best light, so when anyone is searching for you they see good things. This is a combination of online reputation management and search engine optimization for your brand: YOU.
- If you ever stumble upon someone using your likeness in the social media, be very persistent in contacting the site’s administrators. They too have reputations to manage and if they see someone using your photo or likeness they would be smart to delete the stolen profile.
- Or do nothing and don’t worry about it. But when some other John Doe does something stupid or uses your name in a disparaging way or for identity theft, and people assume that it’s you, remember that I told you so.
- Despite all the work you may do to protect yourself, you still need identity theft protection and Internet security software.
Robert Siciliano, identity theft speaker, discusses social media privacy.
Identity Theft Expert Robert Siciliano
The scourge of identity theft knows no boundaries. It can happen to anyone: rich, poor, good credit, bad credit. Victims include children, the elderly, celebrities and politicians, even the dead. Identity theft may include new account fraud, account takeover, criminal identity theft, business identity theft and medical identity theft. Most of these result in financial loss.
One form of identity theft that is particularly damaging to the victim’s reputation is social media identity theft. Social media identity thieves have various motivations. The most damaging type of social media identity theft occurs when someone poses as you in order to disrupt your life. This disruption can take on many forms. They may harass and stalk you or your contacts, or they may steal your online identity for financial gain.
In the case of St. Louis Cardinals manager Tony La Russa, someone created a Twitter account in his name. La Russa is suing Twitter, claiming the impostor Twitter page damaged his reputation and caused emotional distress. The lawsuit includes a screen shot of three tweets. One, posted on April 19, read, “Lost 2 out of 3, but we made it out of Chicago without one drunk driving incident or dead pitcher.” Apparently, La Russa has had a drunk driving arrest and two Cardinals pitchers have died since 2002. One pitcher died of a heart attack, the other in a drunk driving accident.
There is no limit to the damage someone can do by using your name and picture in order to impersonate you online. In Milwaukee, Wisconsin, an 18 year old student was accused of posing as a girl on Facebook, tricking at least 31 male classmates into sending him naked photos of themselves, and then blackmailing some of these young men for sex acts.
Social media websites were created with the intention of bringing people together in a positive way, but we are beginning to see these sites being used in very sinister ways. The root of the problem is the fact that social media sites are all based on the honor system, with the assumption that people are honestly setting up accounts in their own names. There are few checks and balances in the world of social media, which means that you need to adopt a strategy from yet another form of predator to protect yourself.
There are hundreds or even thousands of social media sites, including Facebook, MySpace, Twitter and YouTube. Even your local newspaper’s website has a place for user comments, and most people would prefer to register their own names before someone else has done so on their behalf.
I have obtained over 200 user names pertaining to my given name in order to mitigate social media identity theft. This may sound obsessive, but the two examples given above are all the proof anyone needs to clamp down on social media. I’m on everything from Affluence.org to Zooomr.com. Some I use, others just have my profile and a link back to my website. I should also mention that there are some hazards involved in such a mission. You may experience a spike in spam, as I did, so I suggest creating an alternate email address. Furthermore, some websites make you join various groups that you don’t have much control over. I’m now a member of some masochistic fetish group of the opposite sex. Not exactly what I signed up for. So be careful.
The goal is to obtain your real first and last name without periods, underscores, hyphens, abbreviations or extra numbers or letters.
- Register your full name and those of your spouse and kids on the most trafficked social media sites, blogs, domains or web based email accounts. If your name is already gone, include your middle initial, a period or a hyphen. It’s up to you to decide whether or not to plug in your picture and basic bio, but consider leaving out your age or birthday.
- Set up a free Google Alerts for your name and get an email every time your name pops up online.
- Set up a free StepRep account for your name. StepRep is an online reputation manager that does a better job than Google Alerts does of fetching your name on the web.
- Consider dropping $65 on Knowem.com. This is an online portal that goes out and registers your name at what they consider the top 120 social media sites. Their top 120 is debatable, but a great start. The user experience with Knowem is relatively painless. There is still labor involved in setting things up and with some of the 120. And no matter what you do, you will still find it difficult to complete the registration with all 120 sites. Some of the social media sites just aren’t agreeable. This can save you lots of time, but is only one part of solving the social media identity theft problem.
- Start doing things online to boost your online reputation. Blogging is best. You want Google to bring your given name to the top of search in its best light, so when anyone is searching for you they see good things. This is a combination of online reputation management and search engine optimization for your brand: YOU.
- If you ever stumble upon someone using your likeness in the social media, be very persistent in contacting the site’s administrators. They too have reputations to manage and if they see someone using your photo or likeness they would be smart to delete the stolen profile.
- Or do nothing and don’t worry about it. But when some other John Doe does something stupid or uses your name in a disparaging way or for identity theft, and people assume that it’s you, remember that I told you so.
- Despite all the work you may do to protect yourself, you still need identity theft protection and Internet security software.
Robert Siciliano, identity theft speaker, discusses social media privacy.