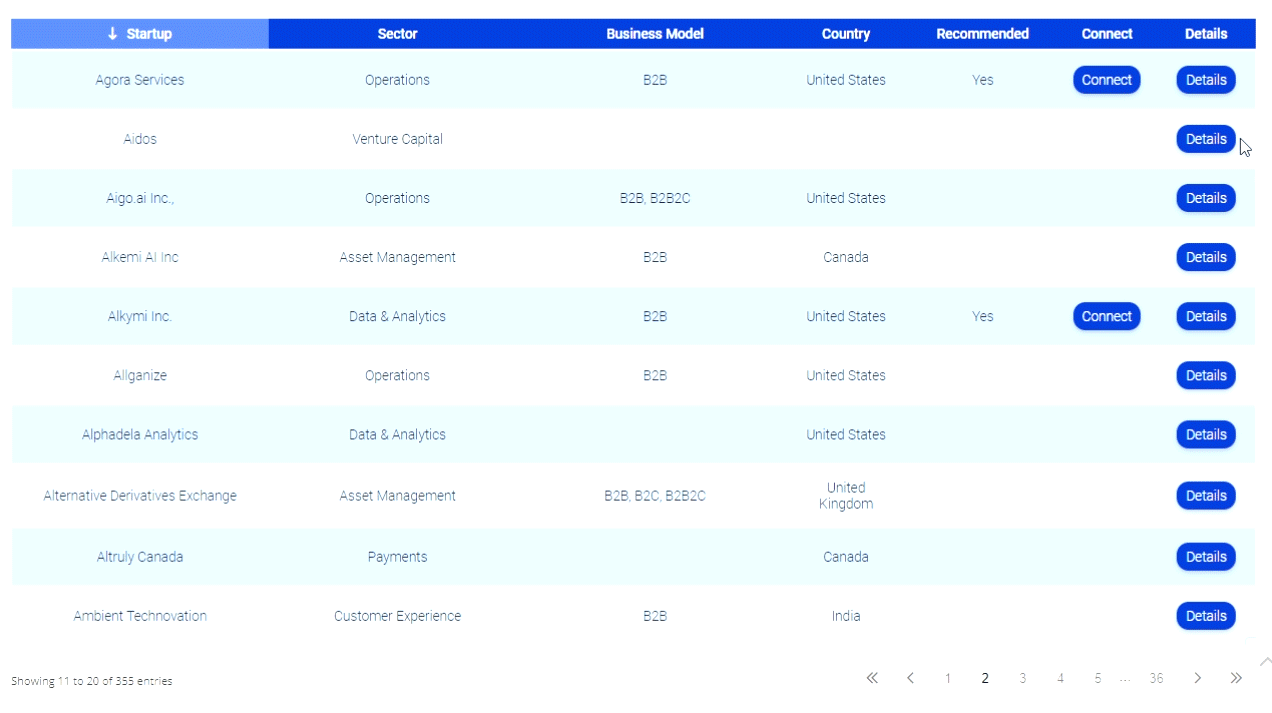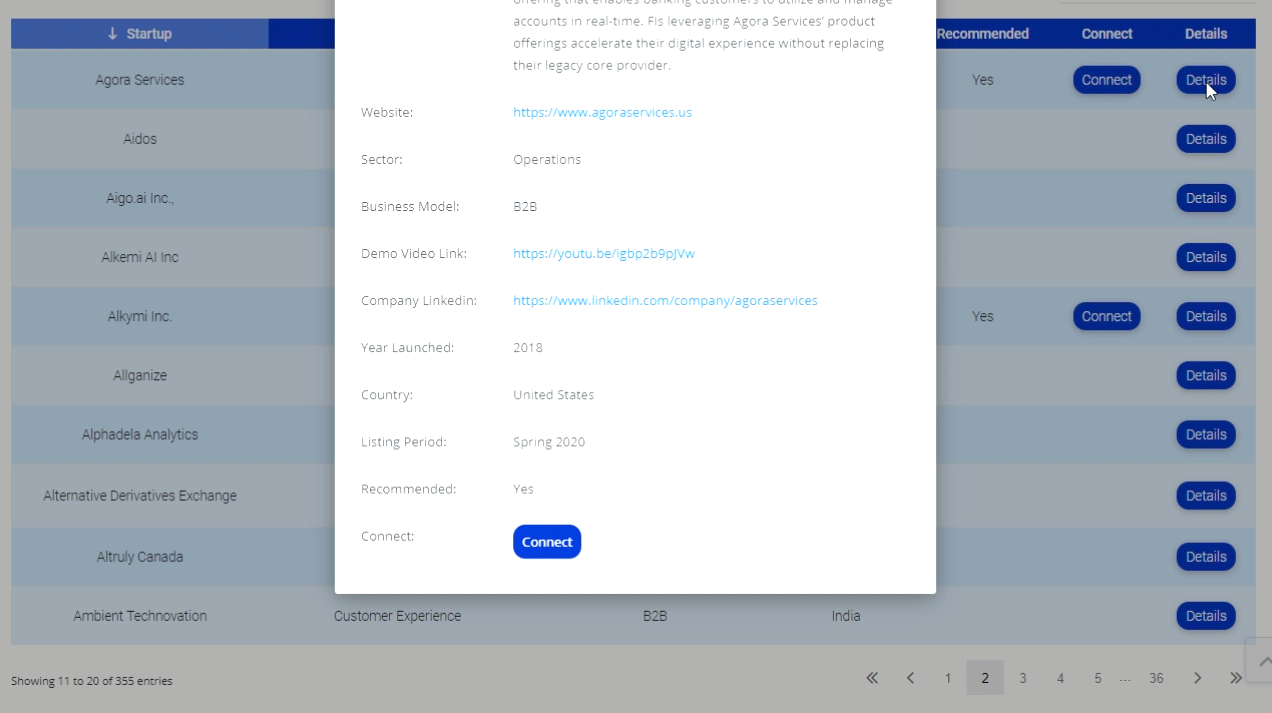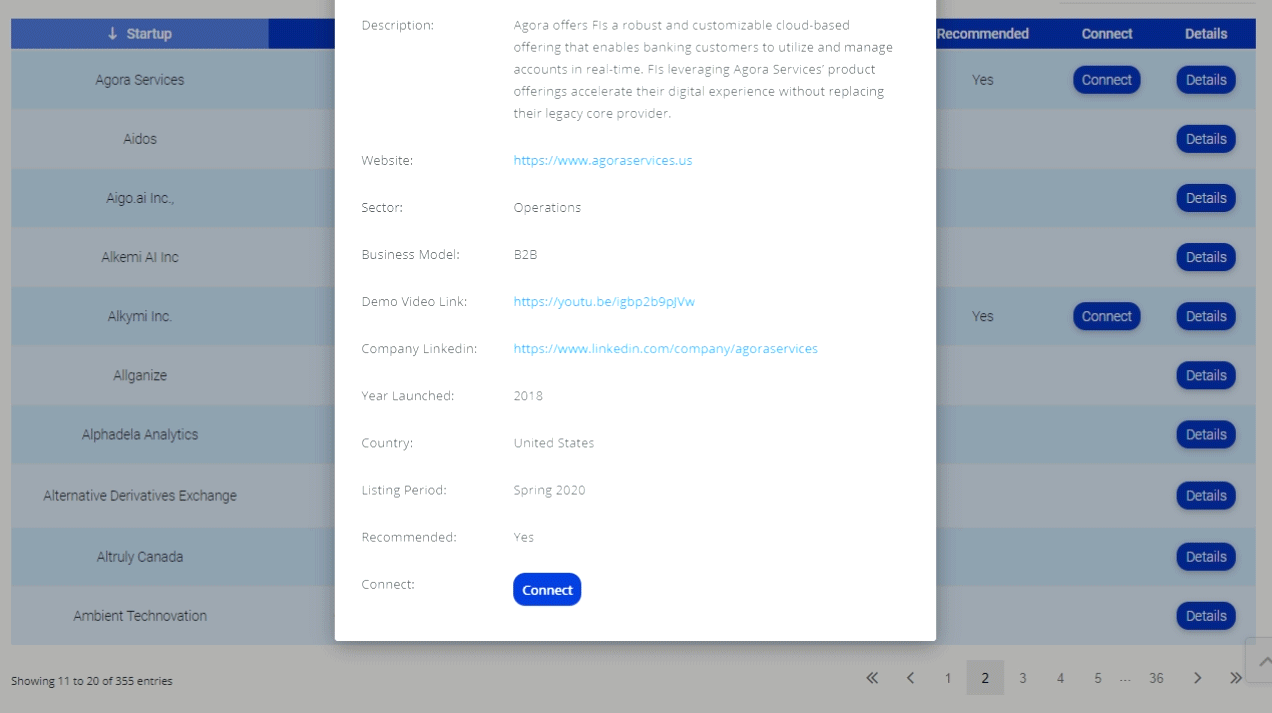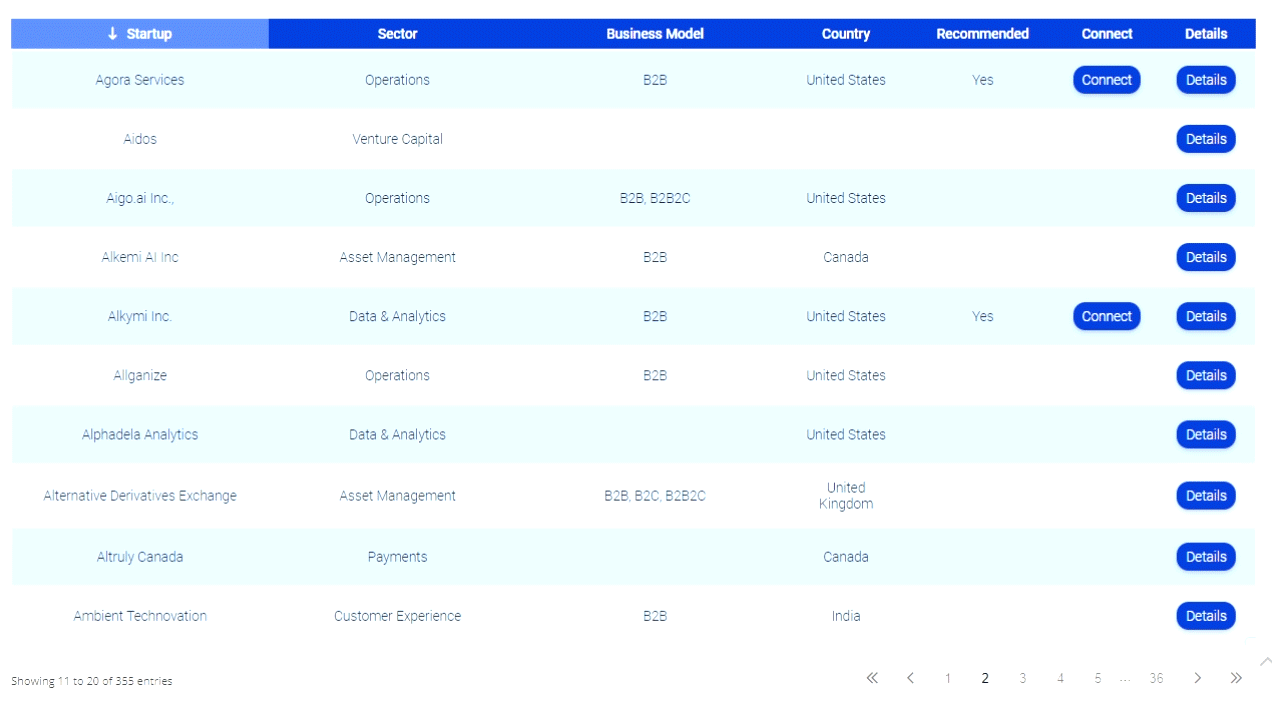
Verifone Goes to War with Square
In a stunning PR/rub-it-in-your-face move, Verifone today launched a broadside attack on startup Square, claiming its mobile payments device contains a “serious security flaw that Square has overlooked that places consumers in dire risk.”
Verifone, which markets a similar produce call PAYware Mobile, even started a website dedicated to blasting at Square.
Here’s the text of the “open letter” Verifone’s CEO wrote today about Square and its security:
Open Letter to the Industry and Consumers
Today is a wake-up call to consumers and the payments industry. Last year, a start-up named Square introduced a credit card reader for smartphones with the goal of making it very easy for anyone to accept credit cards through a mobile device. Seems like a great idea, but there is a serious security flaw that Square has overlooked that places consumers in dire risk.
In less than an hour, any reasonably skilled programmer can write an application that will “skim” – or steal – a consumer’s financial and personal information right off the card utilizing an easily obtained Square card reader. How do we know? We did it. Tested on sample Square card readers with our own personal credit cards, we wrote an application in less than an hour that did exactly this.
Let me explain how easy it is to exploit the vulnerability.
A criminal signs up with Square, obtains the dongle for free and creates a fake Square app on his smartphone. Insert the dongle into the audio jack of a smartphone or iPad, and you’ve got a mobile skimming device that fits in your pocket and that can be used to illegally collect personal and financial data from the magnetic stripe of a payment card. It’s shockingly simple.
The issue is that Square’s hardware is poorly constructed and lacks all ability to encrypt consumers’ data, creating a window for criminals to turn the device into a skimming machine in a matter of minutes.
There are hundreds of thousands of these unsecure devices already floating out there and more are given away for free every day. And because anyone can get their hands on these Square readers, anyone can masquerade as a legitimate business or vendor and swipe your payment card. Your card data is then instantly and illegally captured in the smartphone, un-encrypted – and voila, you’re a fraud victim.
Consumers who hand over their plastic to merchants using Square devices are unwittingly putting themselves in danger.
Don’t take our word for it. See for yourself by downloading the sample skimming application and viewing a video of this type of fraud in action.
Today we are handing a copy of the application over to Visa, MasterCard, Discover, American Express, and JP Morgan Chase (Square’s credit card processor), and we invite their comments.
Consumer trust is what’s really at stake. If the industry allows Square and other similar attempts to short-circuit security best practices, it will seriously jeopardize the integrity and security of the payment infrastructure and financial systems developed over the last three decades.
Secure payment systems, like those provided by VeriFone and other credible providers which adhere to the highest level of security practices, are critical in protecting consumers, merchants and banks. Without this protection, all commerce – conducted with plastic or mobile devices – is a catalyst for massive personal and institutional financial loss.
There is great promise in the future of mobile payments and our innovations will help drive the industry forward. It is our hope that both consumers and merchants will take it upon themselves to become educated on the security risks involved with some of these experimental payment acceptance methods, like Square, and make informed decisions to protect themselves and their customers.
We take security very seriously. Securing payment transactions is what we do, and yes – calling attention to and protecting against these types of security threats to consumers, merchants and banks is our responsibility.
We call on Square to do the responsible thing and recall these card skimming devices from the market.
Douglas G. Bergeron
Chief Executive Officer
So far, the blogophere is coming out with mixed reviews of Verifone’s mudslinging. You can find some good background on the Verifone-Square fight from Computerworld here. Fast Company has a fine breakdown of the arguments Verifone is making, and the questions Square needs to answer here. Mobile Crunch is less equitable. It simply lambastes Verifone for its attacks here. An excerpt:
Here’s the thing: every single time you hand over your credit card to someone (be it someone using Square, or any one of the dozens of other credit card input methods) you’re trusting them not to steal it.
Hand your credit card to a waiter at a restaurant? 9 times out of 10, they walk off with your card for a few minutes. They’re probably just swiping it through their point of sales machine — but they could just as easily be taking it into a back room and jotting down the details on paper. Security flaw!
Oh, and that point of sales machine? It could use an ultra-encrypted mega security reader — but it could just as easily be (and often is) using an ultra simple USB Mag Stripe reader without any sort of encryption whatsoever. All it takes is one rogue employee dumping data into a text file.Security flaw!
Order a pizza for delivery, but want to pay with credit card? At the grocery store, but the power is out? Don’t worry! They’ve got a manual credit card machine, which copies everything from your card onto a piece of carbon paper with one quick swipe. Security flaw!
Ordering something online that isn’t from a major retailer? Unless you’re a techie, how can you confirm that they’re not just harvesting credit cards? Even if they’ve got the same “We’re secured with 8-billion bit encryption!” graphics you’ve seen around the internet, would even a small chunk of the population know how to verify that they’re more than static graphics? Security flaw!
That phony Square app VeriFone built? VeriFone’s own app allows you to punch in credit card numbers manually. An app that looks like VeriFone’s could be built just as easily as an app that resembles Square’s. Security flaw!
See my point? This is a flaw inherent to the entire industry.
We don’t claim to be security experts here at Bank Innovation, but this whole attack by Verifone is probably part true, part smoke-and-mirrors. I am, however, surprised that Verifone — an established banking technology provider that took a big leap forward by agreeing to purchase Hypercom last fall — would play it like this. Such a PR move is the Corporate America equivalent of a leak to Page Six about Charlie Sheen, and it’s difficult to see a place for such practices in banking.