Protect Yourself from Social Engineering
Robert Siciliano Identity Theft Expert
Social engineering is the act of manipulating people into performing actions or divulging confidential information. While similar to a confidence trick or simple fraud, the term typically applies to trickery or deception for the purpose of information gathering, fraud, or computer system access; in most cases the attacker never comes face-to-face with the victim. But in many cases the attacker certainly does come in contact with the victim.
You may be doing all you can and should to protect yourself from hackers and scammers. But a response to a simple email that looks exactly like your expected monthly bank e-statement can completely drain your bank account. On its face there is no way to tell if the communication is real of fake. While hovering over the link may provide a clue, there’s really no way in differentiating all the 1’s and zeros in a typosaquatted domain.
It amazes me that my bank and credit card company still put links in monthly e-statements.
Social engineering has always been a “person to person” confidence crime. Once the conman gains the marks trust, the victim begins to “throw up” all kinds of information or begins to fork over cash and credit. Trust seems to be an inherent trait we all have from birth. I would suppose we would need to trust in order to survive as an interdependent communal species’, otherwise fear of others and not trusting would prevent us from relying on others to nurture us until we are tossed out of the nest.
The conman knows this and the heartless bastard takes full advantage of our trusting nature. Heck, I pulled it off on 2 woman by saying I was from the water company and walked right into there homes.
In the IT world social engineering is a huge problem because the conman doesn’t just access one bank account as in a one on one scam, he accesses thousands by scamming one IT admin or the secretary.
There is a tremendous amount of redundant security in place today that is often completely bypassed because of a simple lie and one naïve gullible person. The path of least resistance isn’t through an unpatched network, or an unsecured wireless connection, it’s via the phone, email, snail mail, social media or in person with a wink and a smile.
Check out this very comprehensive article by Computerworld and these two recent posts here and here.
- Get a credit freeze. Go to ConsumersUnion.org and follow the steps for your particular state. This is an absolutely necessary tool to secure your credit. In most cases, it prevents new accounts from being opened in your name. This makes your Social Security number useless to a potential identity thief. Invest is a social media identity theft protection toll such as Knowem.com.
- Invest in Intelius identity theft protection and prevention. Not all forms of identity theft protection can be prevented, but identity theft protection services can dramatically reduce your risk. (Disclosures)
Robert Siciliano Identity Theft Speaker discussing being an imposter and home invasions on the Montel Williams Show
Robert Siciliano Identity Theft Expert
Social engineering is the act of manipulating people into performing actions or divulging confidential information. While similar to a confidence trick or simple fraud, the term typically applies to trickery or deception for the purpose of information gathering, fraud, or computer system access; in most cases the attacker never comes face-to-face with the victim. But in many cases the attacker certainly does come in contact with the victim.
You may be doing all you can and should to protect yourself from hackers and scammers. But a response to a simple email that looks exactly like your expected monthly bank e-statement can completely drain your bank account. On its face there is no way to tell if the communication is real of fake. While hovering over the link may provide a clue, there’s really no way in differentiating all the 1’s and zeros in a typosaquatted domain.
It amazes me that my bank and credit card company still put links in monthly e-statements.
Social engineering has always been a “person to person” confidence crime. Once the conman gains the marks trust, the victim begins to “throw up” all kinds of information or begins to fork over cash and credit. Trust seems to be an inherent trait we all have from birth. I would suppose we would need to trust in order to survive as an interdependent communal species’, otherwise fear of others and not trusting would prevent us from relying on others to nurture us until we are tossed out of the nest.
The conman knows this and the heartless bastard takes full advantage of our trusting nature. Heck, I pulled it off on 2 woman by saying I was from the water company and walked right into there homes.
In the IT world social engineering is a huge problem because the conman doesn’t just access one bank account as in a one on one scam, he accesses thousands by scamming one IT admin or the secretary.
There is a tremendous amount of redundant security in place today that is often completely bypassed because of a simple lie and one naïve gullible person. The path of least resistance isn’t through an unpatched network, or an unsecured wireless connection, it’s via the phone, email, snail mail, social media or in person with a wink and a smile.
Check out this very comprehensive article by Computerworld and these two recent posts here and here.
- Get a credit freeze. Go to ConsumersUnion.org and follow the steps for your particular state. This is an absolutely necessary tool to secure your credit. In most cases, it prevents new accounts from being opened in your name. This makes your Social Security number useless to a potential identity thief. Invest is a social media identity theft protection toll such as Knowem.com.
- Invest in Intelius identity theft protection and prevention. Not all forms of identity theft protection can be prevented, but identity theft protection services can dramatically reduce your risk. (Disclosures)
Robert Siciliano Identity Theft Speaker discussing being an imposter and home invasions on the Montel Williams Show




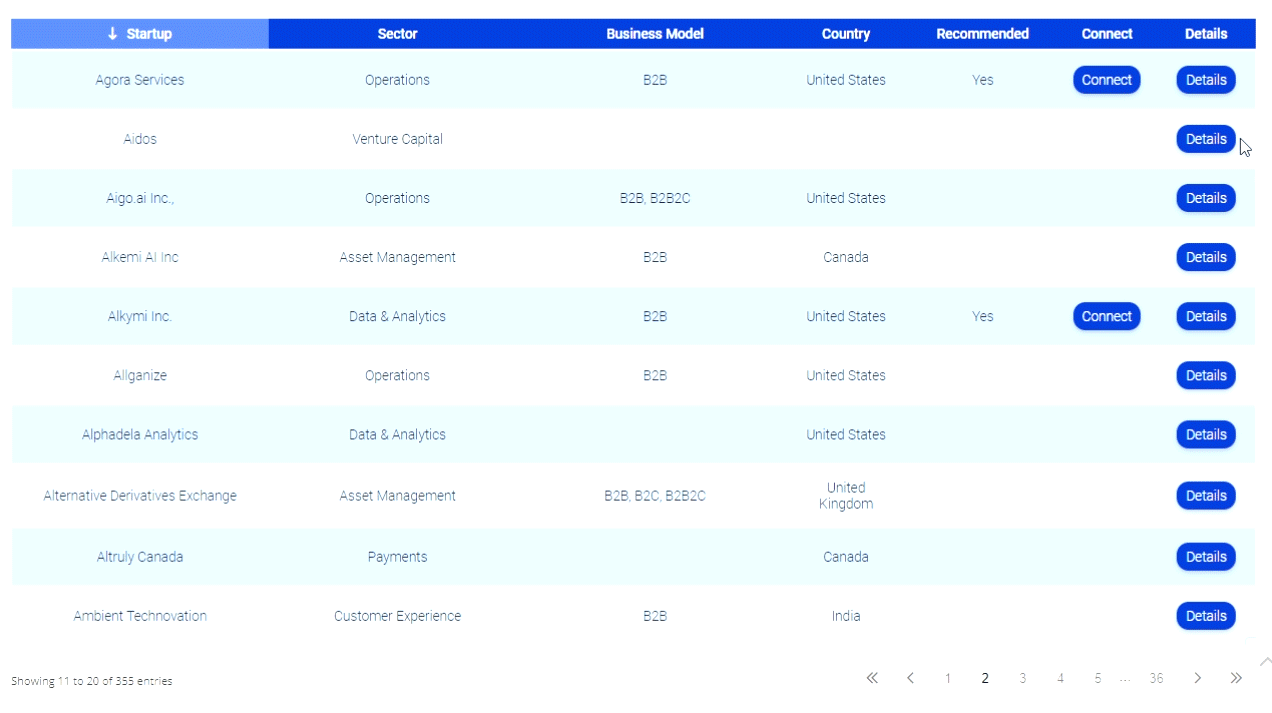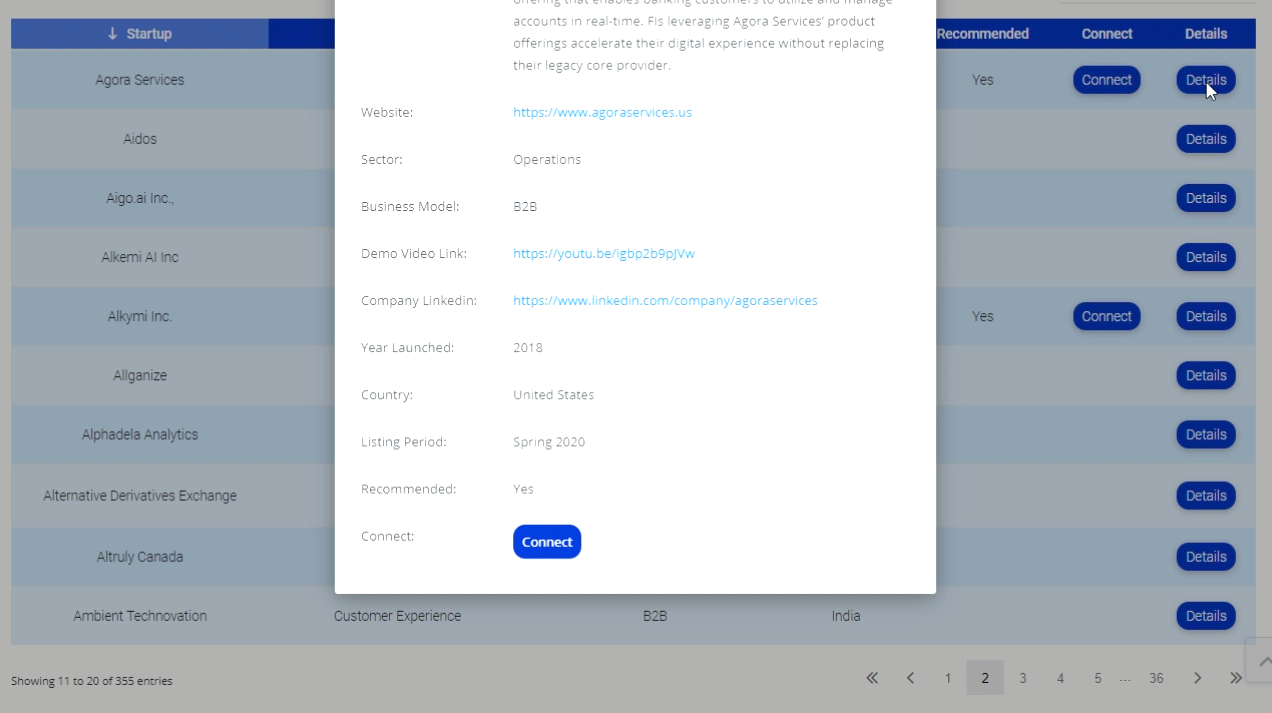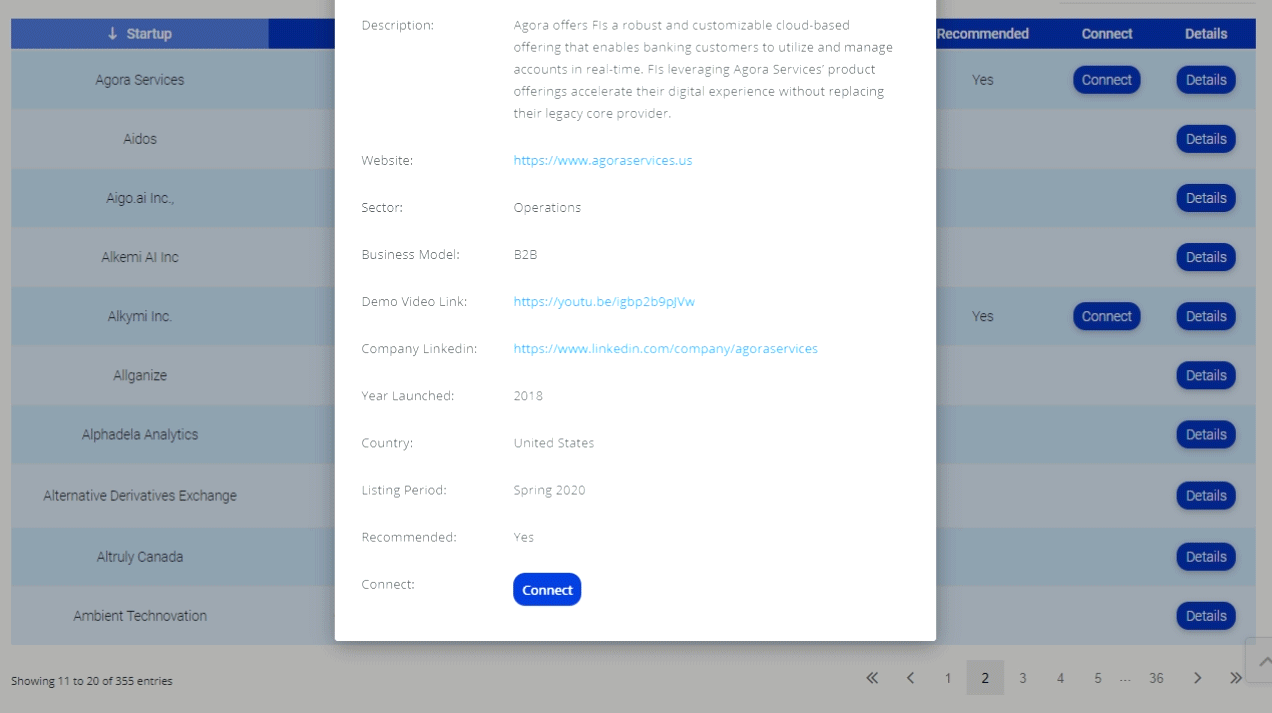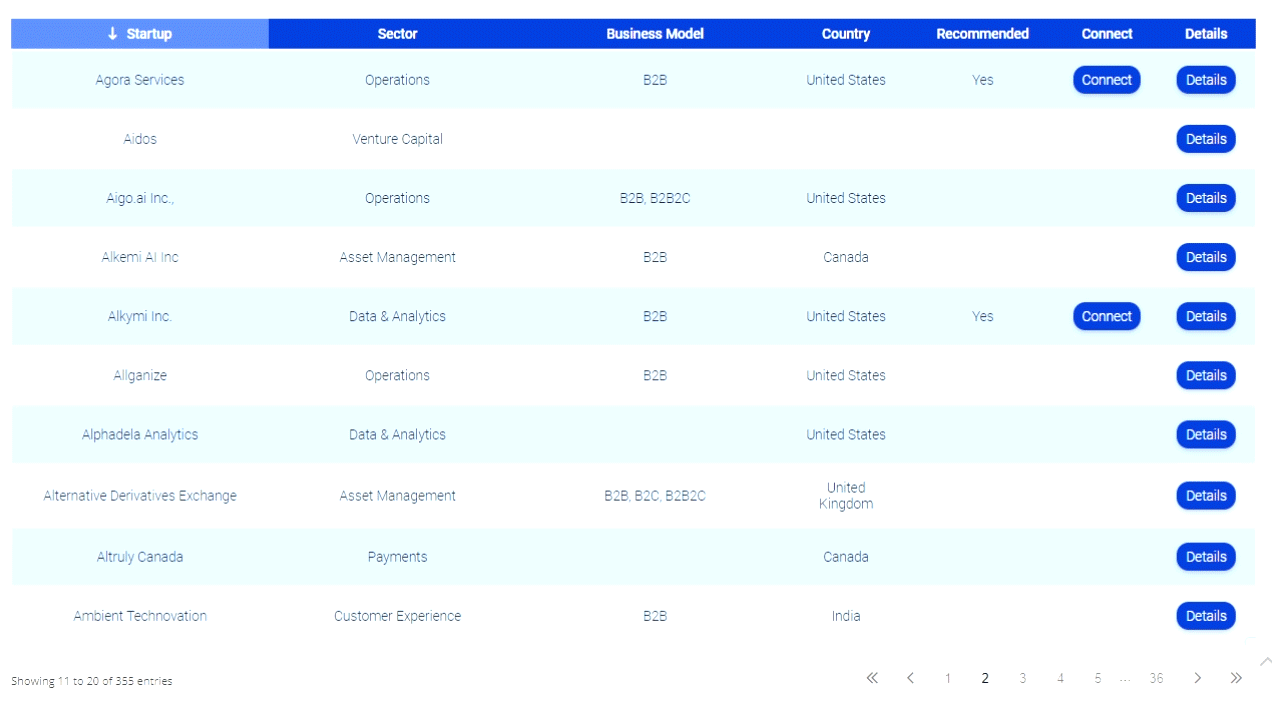







If you are a man with spinal cord do not fall into that. People need to think not influenced to leave.