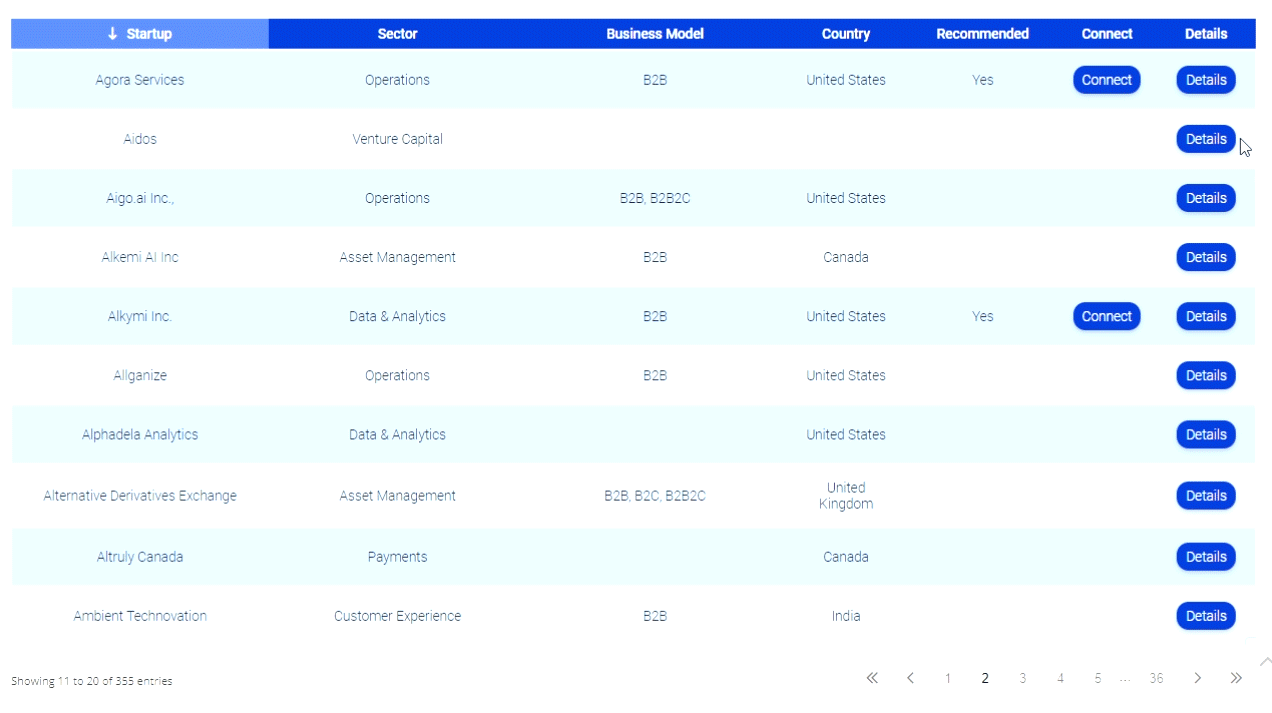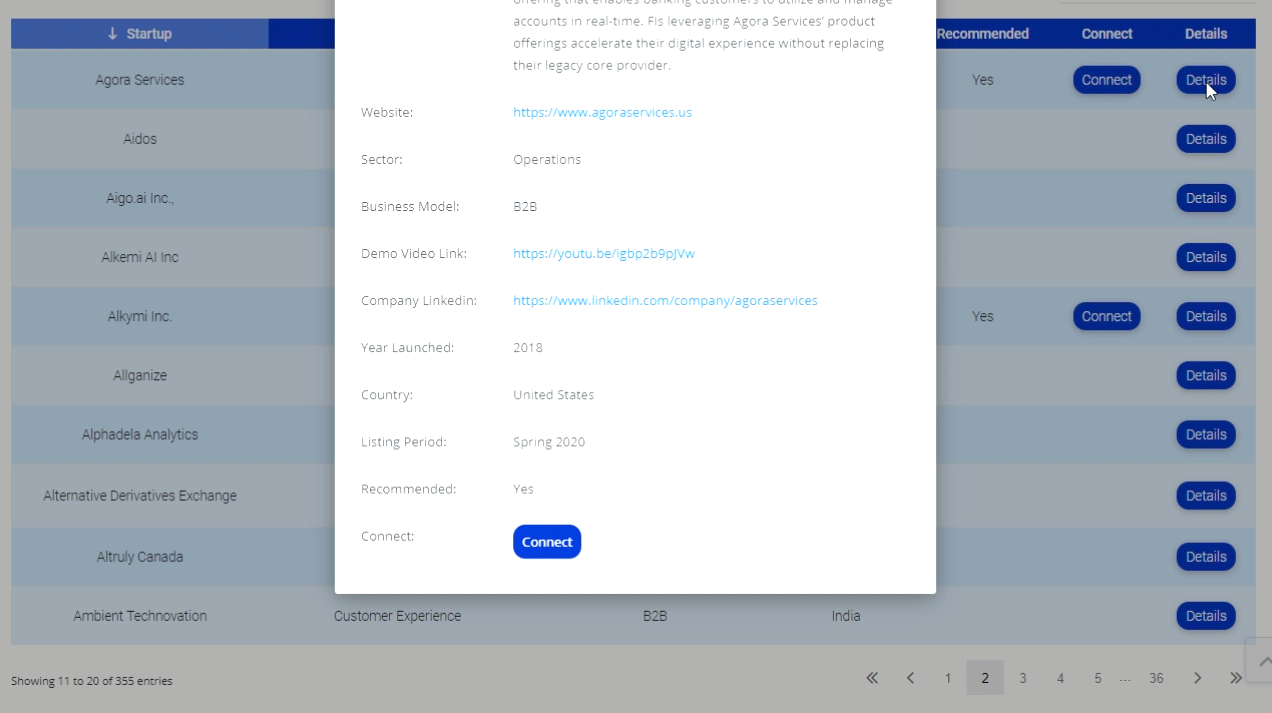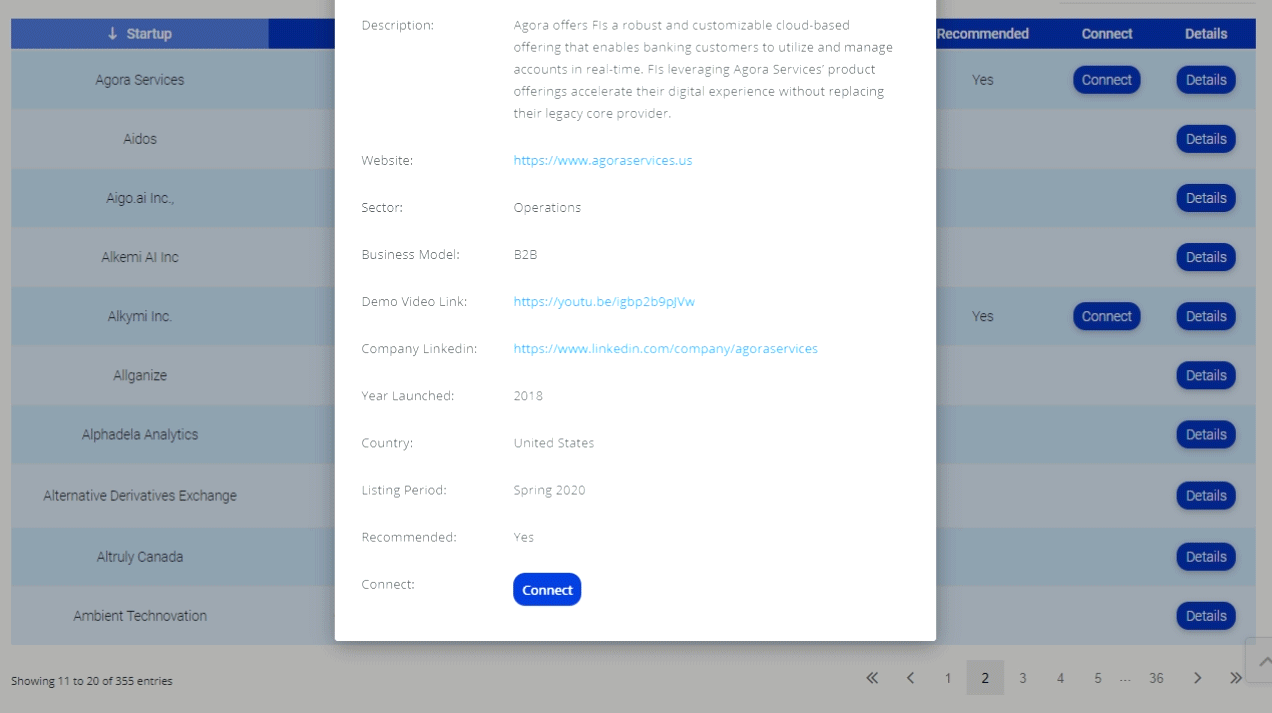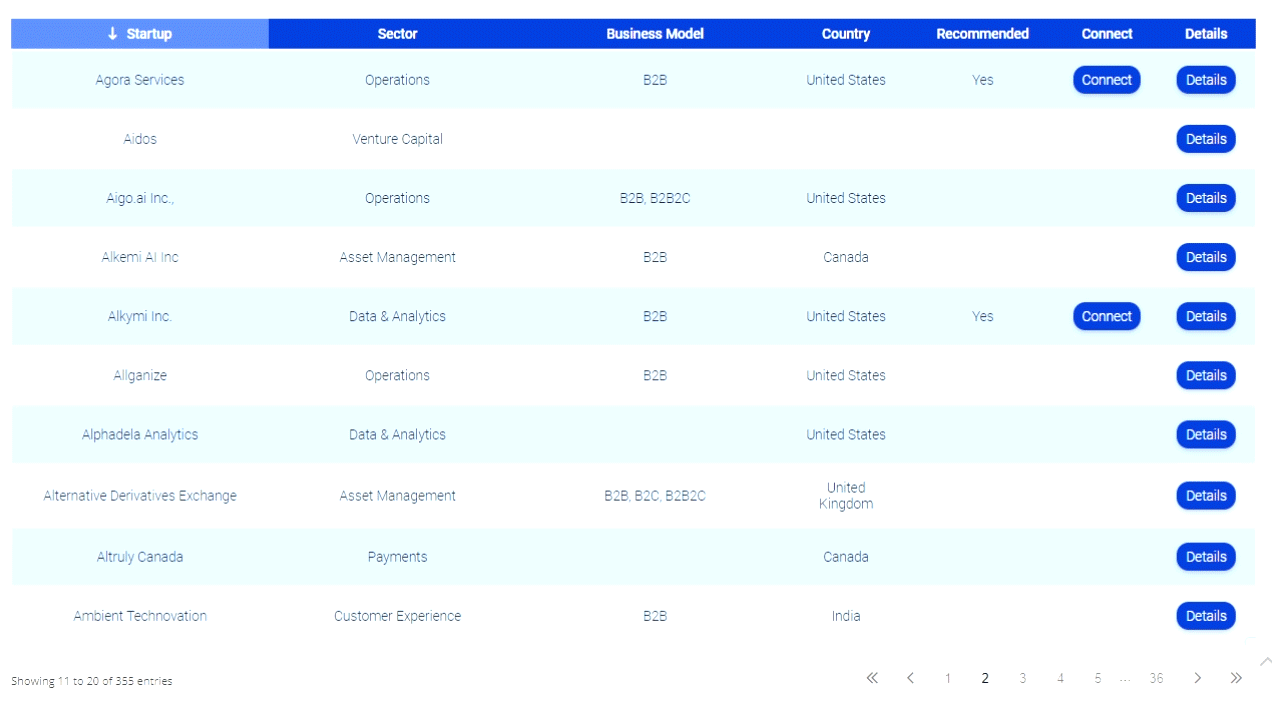
PC Worlds Top 10 Security Nightmares of the Decade
Robert Siciliano Identity Theft Expert
The last decade we have seen technological breakthroughs unlike any other. In response we have seen a tremendous rise in fraud. The reason? The speed of the conveniences technology have far outpaced the security of technology.
Cyberwar: In February 2000, a Canadian teenager named Mafiaboy used automated floods of incomplete Internet traffic to cause several sites–including Amazon, CNN, Dell, eBay, and Yahoo–to grind to a halt, in what is called a distributed denial of attack.
Malware: Viruses and worms have always been around, but in the summer of 2001 one aggressive worm threatened to shut down the official White House Website.
MySpace, Facebook, and Twitter Attacks: At the beginning of the decade, security experts at businesses had to struggle with employees’ use of instant messaging from AOL, Webmail from Yahoo, and peer-to-peer networks. These applications poked holes in corporate firewalls, opening various ports that created new vectors for malware.
Organized Viruses and Organized Crime: After the Melissa virus struck in 1999, e-mail-borne viruses peaked the following year with ILOVEYOU, which clogged e-mail servers worldwide within 5 hours. (See “The World’s Worst Viruses” for more about a clutch of the decade’s early offenders.)
Botnets: With the financial backing of organized crime syndicates came widespread and clever innovations in malware.
Albert Gonzalez: It wasn’t organized crime but rather a confederacy of criminals that caused some of the largest data breaches over the last few years–attacks that victimized Dave & Busters, Hannaford Brothers, Heartland Payment Systems, and TJX, to name just a few.
Gone Phishing: More effective than spam, yet short of a full-blown data breach, is phishing. The idea here is that a creatively designed e-mail can lure you into visiting a believable-looking site designed solely to steal your personal information.
Old Protocol, New Problem: Behind the Internet are protocols, some of which today perform functions far beyond what they were originally designed to do. Perhaps the most well-known of the overextended protocols is the Domain Name System (DNS), which, as IOActive researcher Dan Kaminisky explained in 2008, could be vulnerable to various forms of attack, including DNS cache poisoning.
Microsoft Patch Tuesdays: A decade ago, Microsoft released its patches only as needed. Sometimes that was late on a Friday afternoon, which meant that bad guys had all weekend to reverse-engineer the patch and exploit the vulnerability before system administrators showed up for work on Monday.
Paid Vulnerability Disclosure: Independent researchers have debated for years whether to go public with a newly found flaw or to stay with the vendor until a patch is created.
Protect your identity. Go to ConsumersUnion.org and follow the steps for your particular state. This is an absolutely necessary tool to secure your credit. In most cases, it prevents new accounts from being opened in your name. This makes your Social Security number useless to a potential identity thief.
Invest in Intelius identity theft protection and prevention. Not all forms of identity theft protection can be prevented, but identity theft protection services can dramatically reduce your risk. (Disclosures)
Robert Siciliano identity theft speaker discussing credit card fraud on CNBC