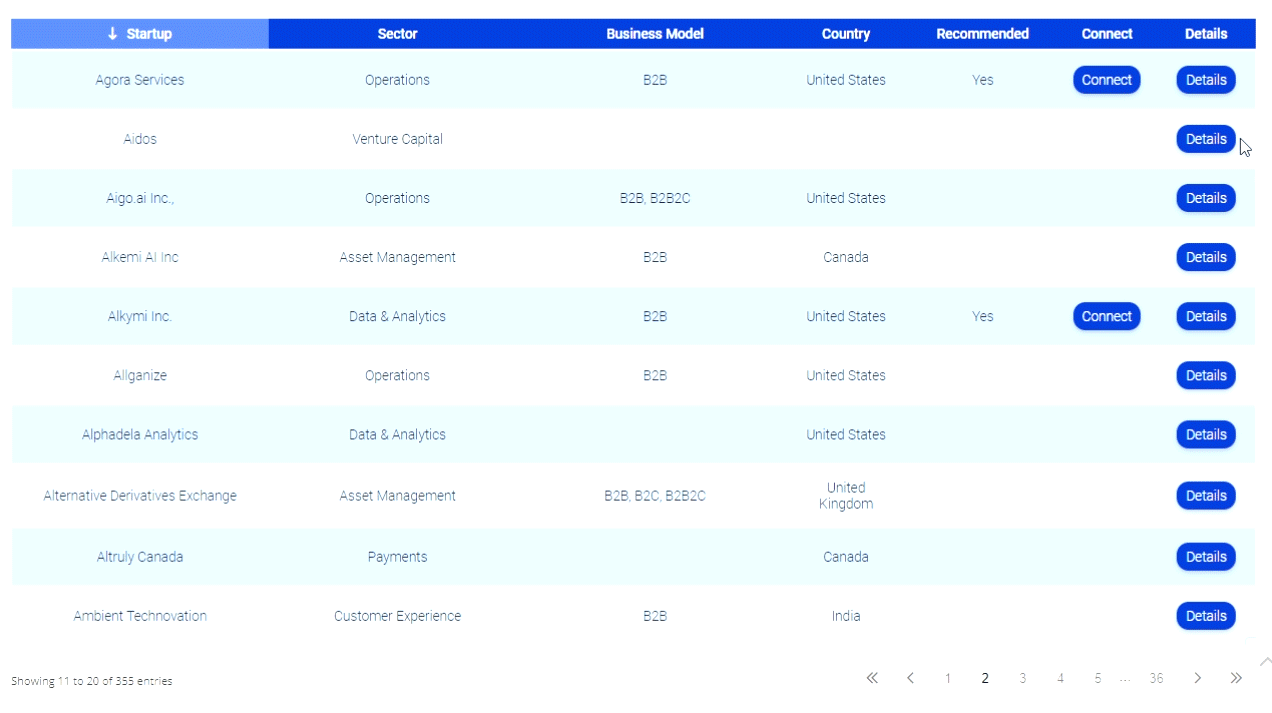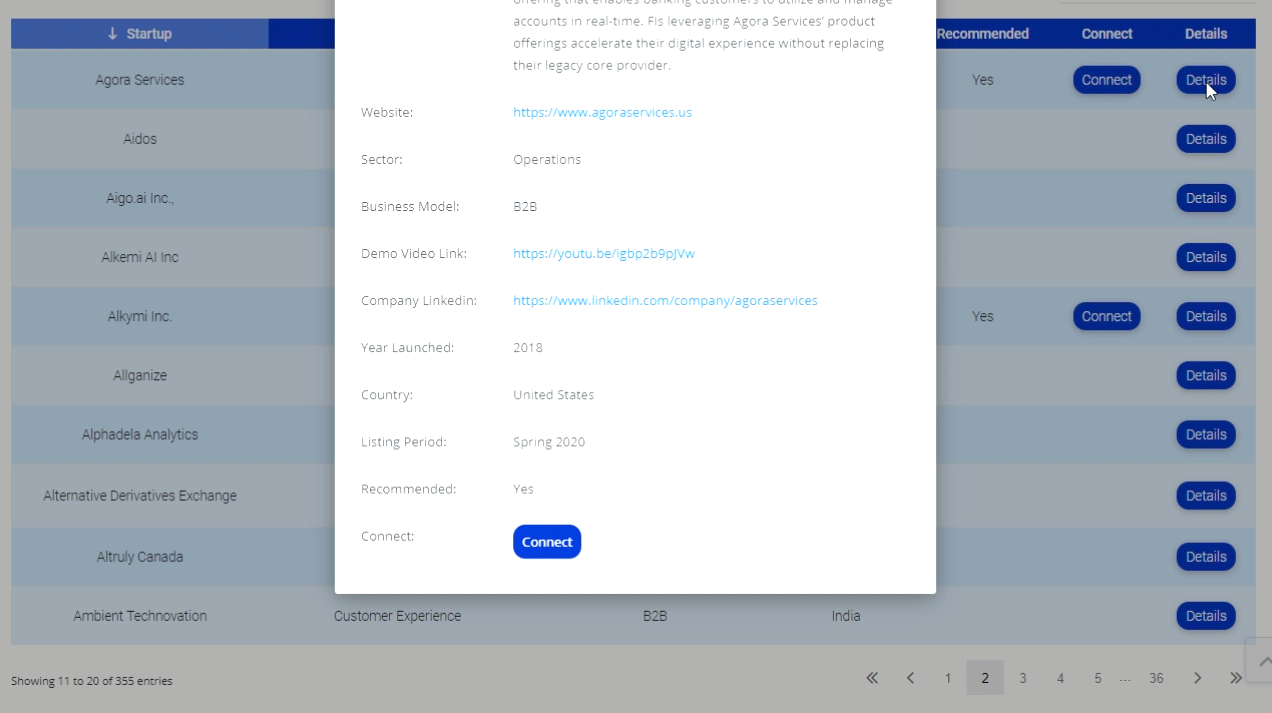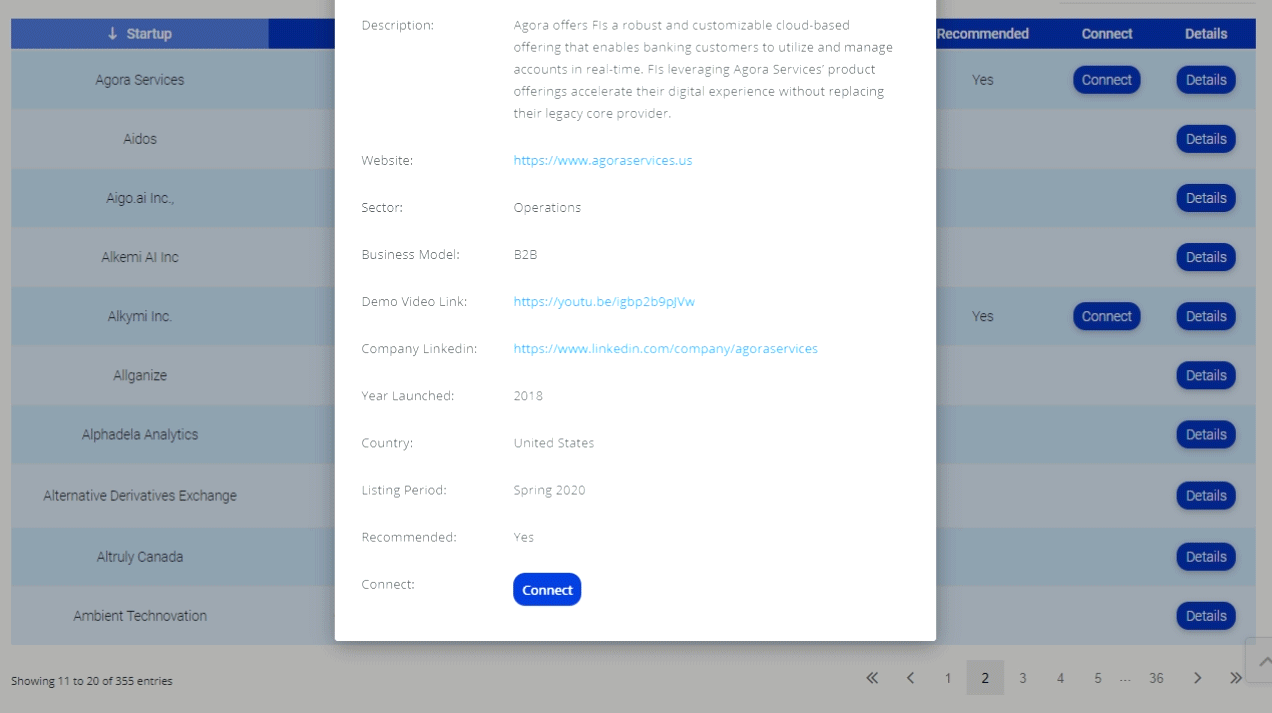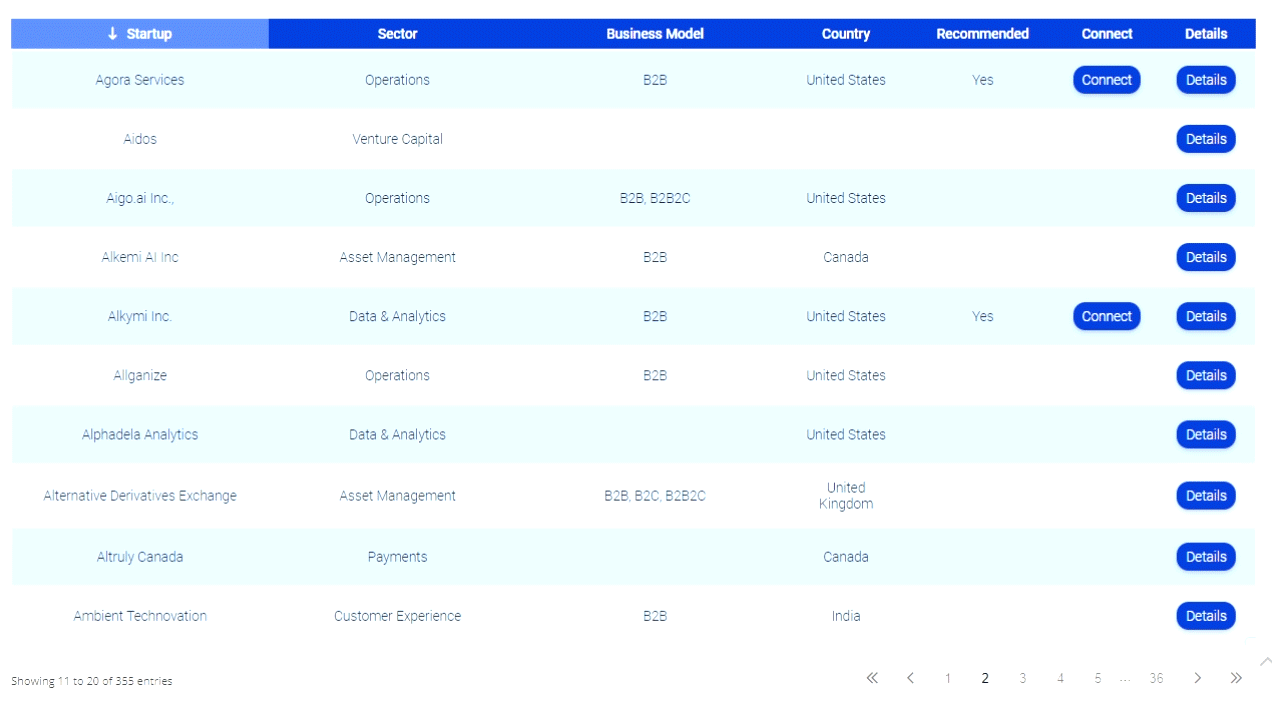
MIT Says Handing Over Your Identity Data Protects You
Robert Siciliano Identity Theft Expert
Identity is a simple concept that has become a complex problem. It has become complex due to fraud. Fraud, motivated by money and the ease of obtaining credit and taking over an account. Because identity has yet to be effectively established, anyone can be you.
Currently, identity is generally established when a person provides a single source of data such as a Social Security number, password, credit card number and so forth. Complicating things further, in the U.S. we have as many as 200 forms of ID circulating from state to state, plus another 14,000 birth certificates and 49 versions of the Social Security card. We use “for profit” third party information brokers and the lowly vital statistics agency that works for each state to manage the data.
According to a new proposal in New Scientist, our digital identities will be more secure if they are based on data from our everyday life, culled from cell phones and online transactions. The idea comes from the Massachusetts Institute of Technology’s Human Dynamics Laboratory. The lab is a pioneer of “reality mining,” which is the practice of studying how people behave by using the crumbs of digital data our actions produce.
Reality mining is “what you do and who you do it with.” Or in MIT-over-my-head-speak: “Reality Mining defines the collection of machine-sensed environmental data pertaining to human social behavior. This new paradigm of data mining makes possible the modeling of conversation context, proximity sensing, and temporospatial location throughout large communities of individuals. Mobile phones are used for data collection, opening social network analysis to new methods of empirical (information gained by means of observation) stochastic (random) modeling.”
Even Google can’t define the word “temporospatial.” Find it. I dare you.
The research is based on the use of mobile phones to provide insight into individual and group behavior. They captured communication, proximity, location, and activity information from 100 subjects at MIT over a year. This data represents over 350,000 hours (~40 years) of continuous data on human behavior. Some of the research questions include:
- How do social networks evolve over time?
- How predictable are most people’s lives?
- How does information flow?
The idea is to capture and harness all this information that represents “what you do and who you do it with.” Managing this would consist of the creation of a central body, supported by a combination of cellphone networks, banks and government bodies. The bank, being one of the supporters, could provide “slices” of data to third parties that want to check a person’s identity.
This is different than “who you are and what you know.” Currently, positive ID is only possible by using a biometric. A biometric can be either static (anatomical, physiological) or dynamic (behavioral). Examples static biometrics include your iris, fingerprint, face, and DNA. Dynamic biometrics include your signature gesture, voice, keyboard, and perhaps gait. Also referred to as something you are. Verification is used when the identity of a person cannot be definitely established. Technologies used provide real time assessment of the validity of an asserted identity. We don’t know who the individual is but we try to get as close as we can to verify his or her asserted identity. Included in this class are out of wallet questions, PINS, passwords, tokens, cards, IP addresses, behavioral based trend data, credit cards, etc. These usually fall into the realm of something you have or something you know.
Currently, identity isn’t established. There is no accountability. That’s why we have identity theft. Anyone can become you just by saying so. In the meantime, until the big heads at MIT figure this out, protect your identity.
Get a credit freeze. Go to ConsumersUnion.org and follow the steps for your particular state. This is an absolutely necessary tool to secure your credit. In most cases, it prevents new accounts from being opened in your name. This makes your Social Security number useless to a potential identity thief.
Invest in Intelius identity theft protection and prevention. Not all forms of identity theft protection can be prevented, but identity theft protection services can dramatically reduce your risk. “Disclosures”
Robert Siciliano, identity theft speaker, discusses Social Security numbers on Fox News
Robert Siciliano Identity Theft Expert
Identity is a simple concept that has become a complex problem. It has become complex due to fraud. Fraud, motivated by money and the ease of obtaining credit and taking over an account. Because identity has yet to be effectively established, anyone can be you.
Currently, identity is generally established when a person provides a single source of data such as a Social Security number, password, credit card number and so forth. Complicating things further, in the U.S. we have as many as 200 forms of ID circulating from state to state, plus another 14,000 birth certificates and 49 versions of the Social Security card. We use “for profit” third party information brokers and the lowly vital statistics agency that works for each state to manage the data.
According to a new proposal in New Scientist, our digital identities will be more secure if they are based on data from our everyday life, culled from cell phones and online transactions. The idea comes from the Massachusetts Institute of Technology’s Human Dynamics Laboratory. The lab is a pioneer of “reality mining,” which is the practice of studying how people behave by using the crumbs of digital data our actions produce.
Reality mining is “what you do and who you do it with.” Or in MIT-over-my-head-speak: “Reality Mining defines the collection of machine-sensed environmental data pertaining to human social behavior. This new paradigm of data mining makes possible the modeling of conversation context, proximity sensing, and temporospatial location throughout large communities of individuals. Mobile phones are used for data collection, opening social network analysis to new methods of empirical (information gained by means of observation) stochastic (random) modeling.”
Even Google can’t define the word “temporospatial.” Find it. I dare you.
The research is based on the use of mobile phones to provide insight into individual and group behavior. They captured communication, proximity, location, and activity information from 100 subjects at MIT over a year. This data represents over 350,000 hours (~40 years) of continuous data on human behavior. Some of the research questions include:
- How do social networks evolve over time?
- How predictable are most people’s lives?
- How does information flow?
The idea is to capture and harness all this information that represents “what you do and who you do it with.” Managing this would consist of the creation of a central body, supported by a combination of cellphone networks, banks and government bodies. The bank, being one of the supporters, could provide “slices” of data to third parties that want to check a person’s identity.
This is different than “who you are and what you know.” Currently, positive ID is only possible by using a biometric. A biometric can be either static (anatomical, physiological) or dynamic (behavioral). Examples static biometrics include your iris, fingerprint, face, and DNA. Dynamic biometrics include your signature gesture, voice, keyboard, and perhaps gait. Also referred to as something you are. Verification is used when the identity of a person cannot be definitely established. Technologies used provide real time assessment of the validity of an asserted identity. We don’t know who the individual is but we try to get as close as we can to verify his or her asserted identity. Included in this class are out of wallet questions, PINS, passwords, tokens, cards, IP addresses, behavioral based trend data, credit cards, etc. These usually fall into the realm of something you have or something you know.
Currently, identity isn’t established. There is no accountability. That’s why we have identity theft. Anyone can become you just by saying so. In the meantime, until the big heads at MIT figure this out, protect your identity.
Get a credit freeze. Go to ConsumersUnion.org and follow the steps for your particular state. This is an absolutely necessary tool to secure your credit. In most cases, it prevents new accounts from being opened in your name. This makes your Social Security number useless to a potential identity thief.
Invest in Intelius identity theft protection and prevention. Not all forms of identity theft protection can be prevented, but identity theft protection services can dramatically reduce your risk. “Disclosures”
Robert Siciliano, identity theft speaker, discusses Social Security numbers on Fox News