mCrimes Morph Into mBotnets
Robert Siciliano Identity Theft Expert
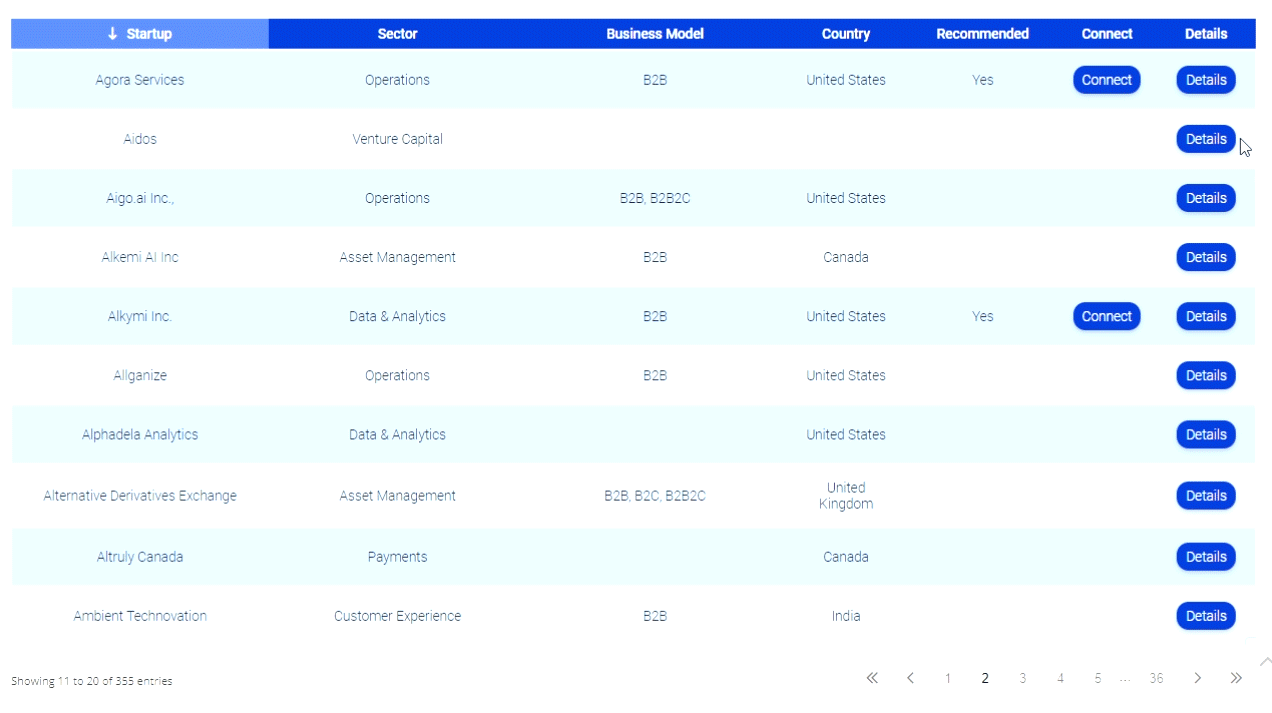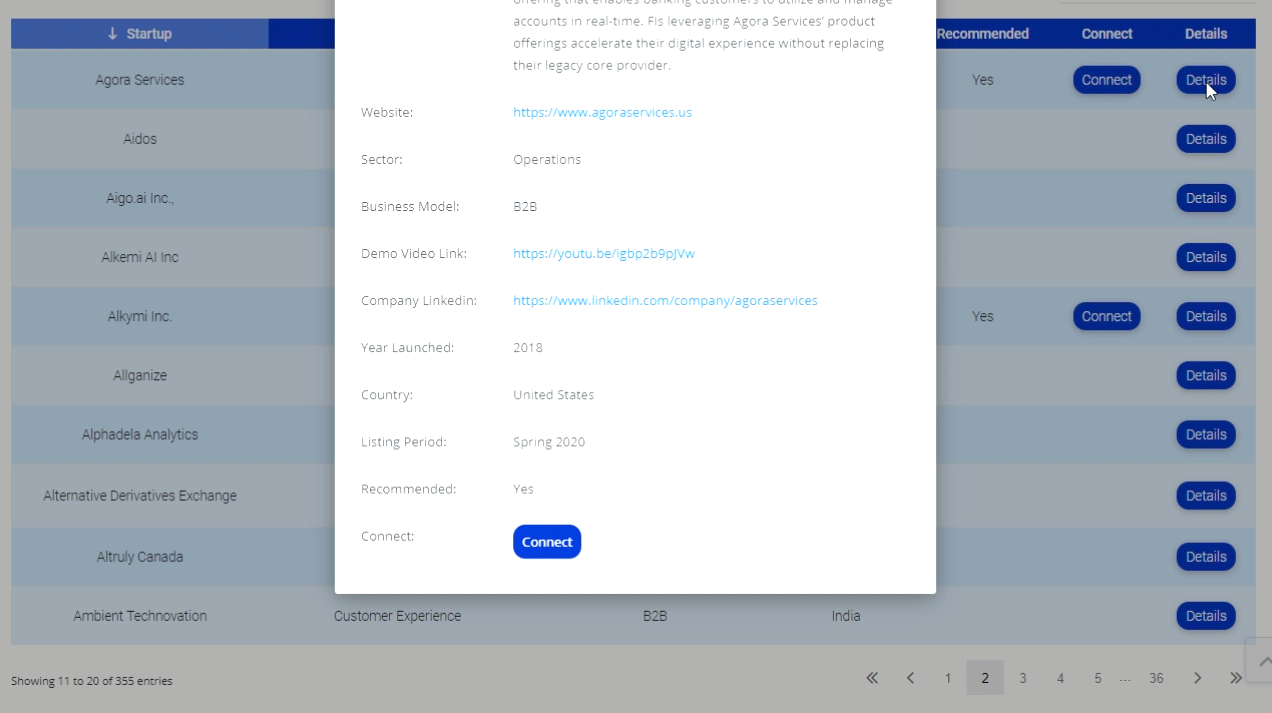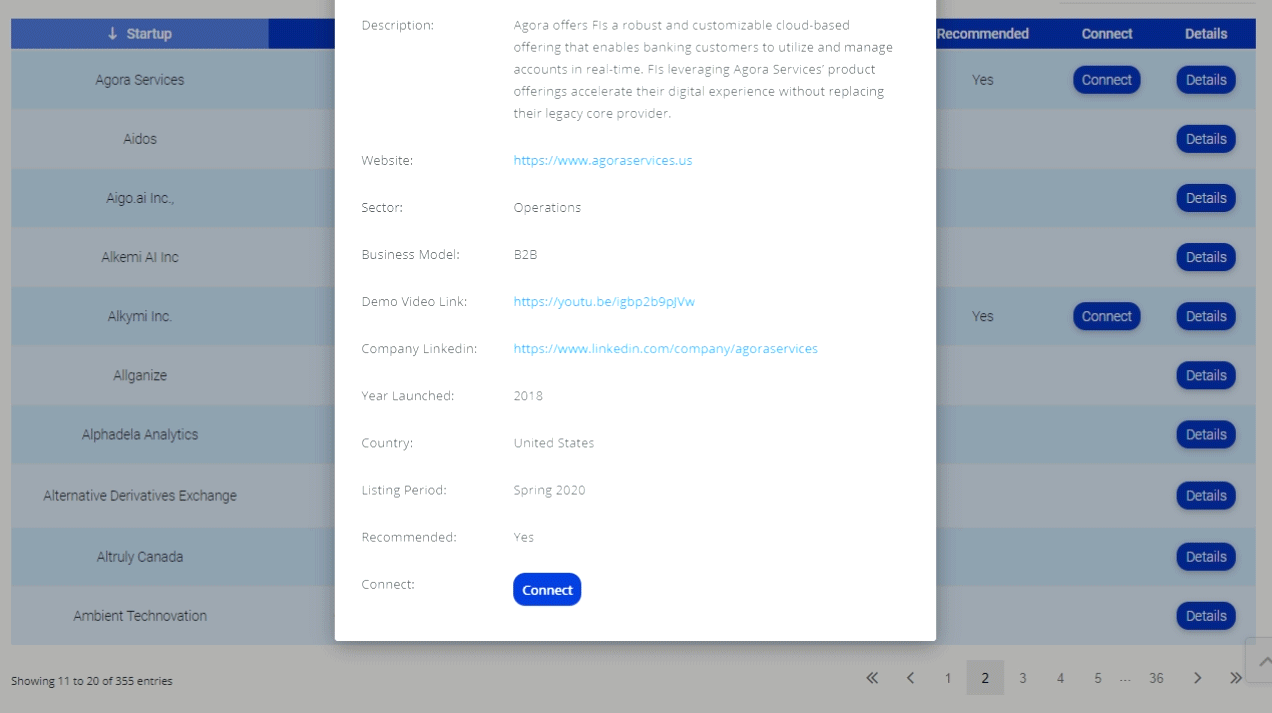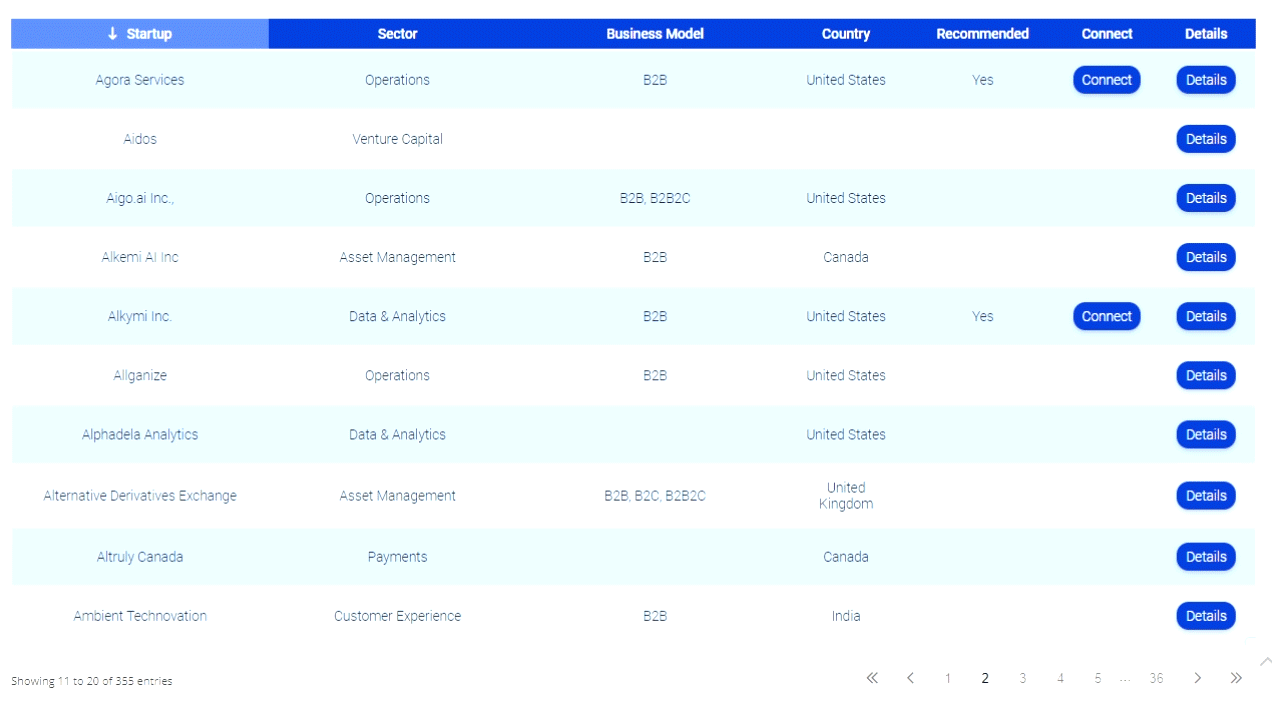
Botnets are robot networks of computers connected to the Internet that sit in our homes and offices. A botnet is generally banks of multiple PC’s from the 10’s to 10,000’s to millions. There are no hard numbers on botnets but last figure I saw was somewhere between 3-5 million. Another stat is 25 percent of all US based PC’s are on a botnet. That’s just insane. Botnets PC’s are called Zombies. Zombies all generally share a virus in common that allows for a remote control component. The criminal hacker controls the zombies on the botnet via an IRC control server or via a peer to peer network.
The combined power of the zombies on the botnet allows the criminals to commit all kinds of crimes such as denial of service attacks, mass spam campaigns of blasting viruses to millions.
Often botnets are used to store stolen data or to host spoofed websites that collect that data.
Now comes “Sexy Space,” an infected text message containing a link that when clicked downloads a file making that phone part of an mBot. mBots are made up of “Zobiles”. The download then infects the users contact list and in typical virus multiplication fashion, sends the Sexy Space text to them too.
It is believed that infected phones could then be used in similar ways as traditional zombies are. The extra twist with a zobile is its ability to take pictures, video, and used as a covert audio listening device. It can also sniff out wireless connections to the Internet and gather additional data to be used to hack.
History indicates that we are at the forefront of an era in which criminal hackers develop tools and techniques to steal your money using your own cell phone. Fifteen years ago, cell phones were bulky and cumbersome, they had to be carried in bags or briefcases. Then they became chunky, heavy bricks. Calls dropped every other minute. Clearly, cell phones have evolved since then. Today’s cell phone is a lot more than a phone. It’s a computer, one that rivals many desktops and laptops being manufactured today.
Never click on links in text messages unless you are 100 percent sure it’s a legitimate communication from a trusted source.
Follow your phones manufacturers and carriers recommendations on securing your phone. A search on “mobile phone security” turns up options/downloads/security to consider.
Protect your identity.
1. Get a credit freeze. Click on the preceding link and follow the steps for your particular state. This is an absolutely necessary tool to secure your credit. In most cases, it prevents new accounts from being opened in your name. This makes your Social Security number useless to a potential identity thief.
2. Invest in anti-virus and keep it auto-updated and check out my spyware killer IDTheftSecurty HERE
3. Go to my website and get my FREE ebook on how to protect yourself from the bad guy.
4. Invest in Intelius identity theft protection and prevention. Not all forms of identity theft can be prevented, but identity theft protection services can dramatically reduce your risk. (Disclosures)
Robert Siciliano Identity Theft Speaker discussing mobile phone crimes and hacking on the Mike and Juliet Show