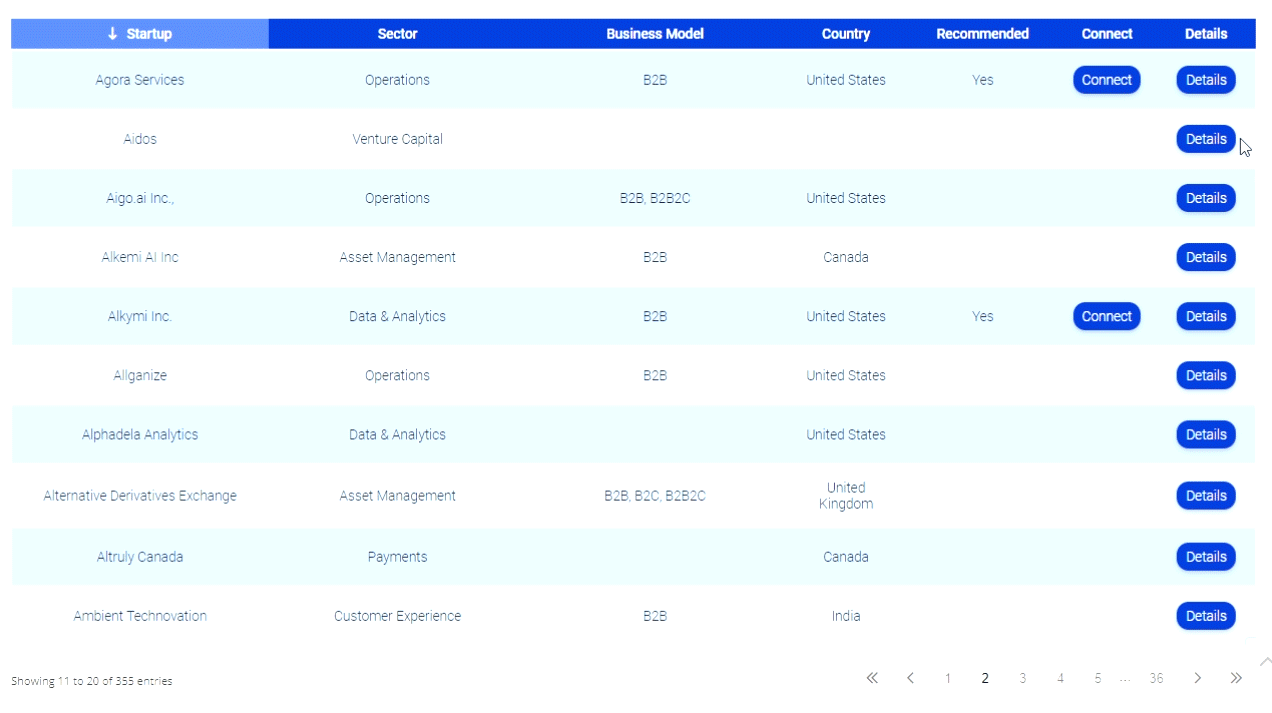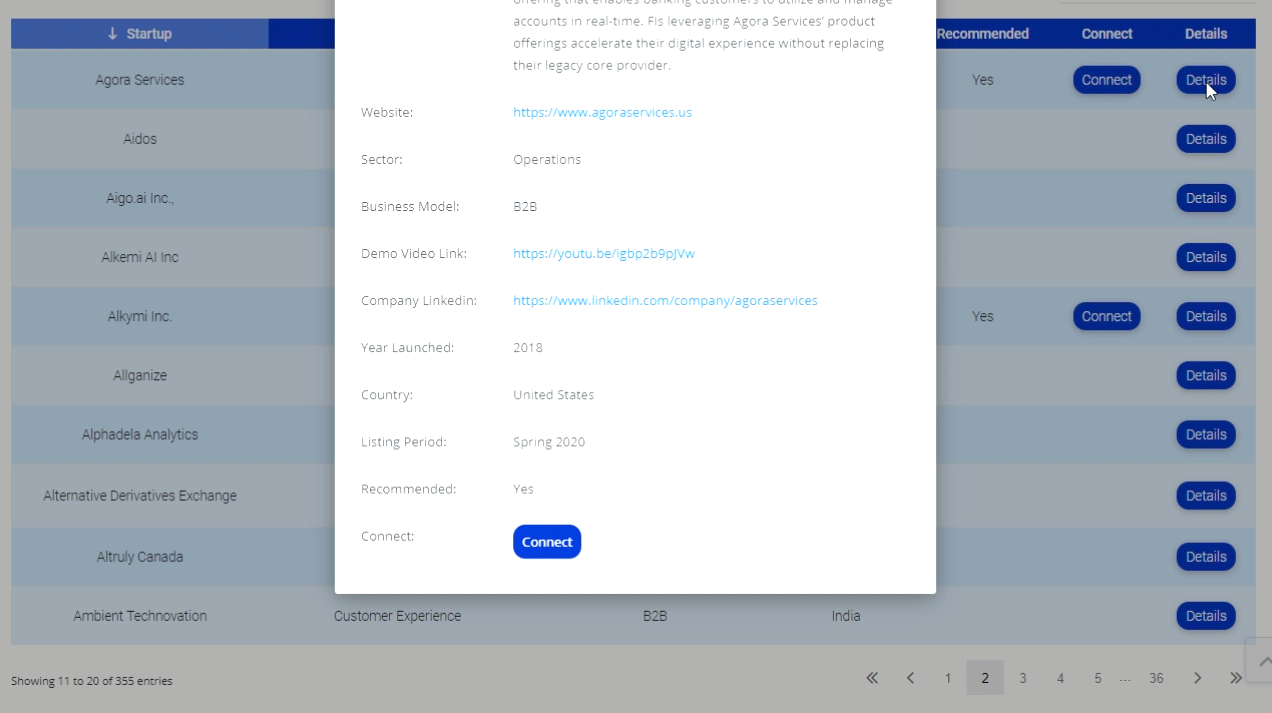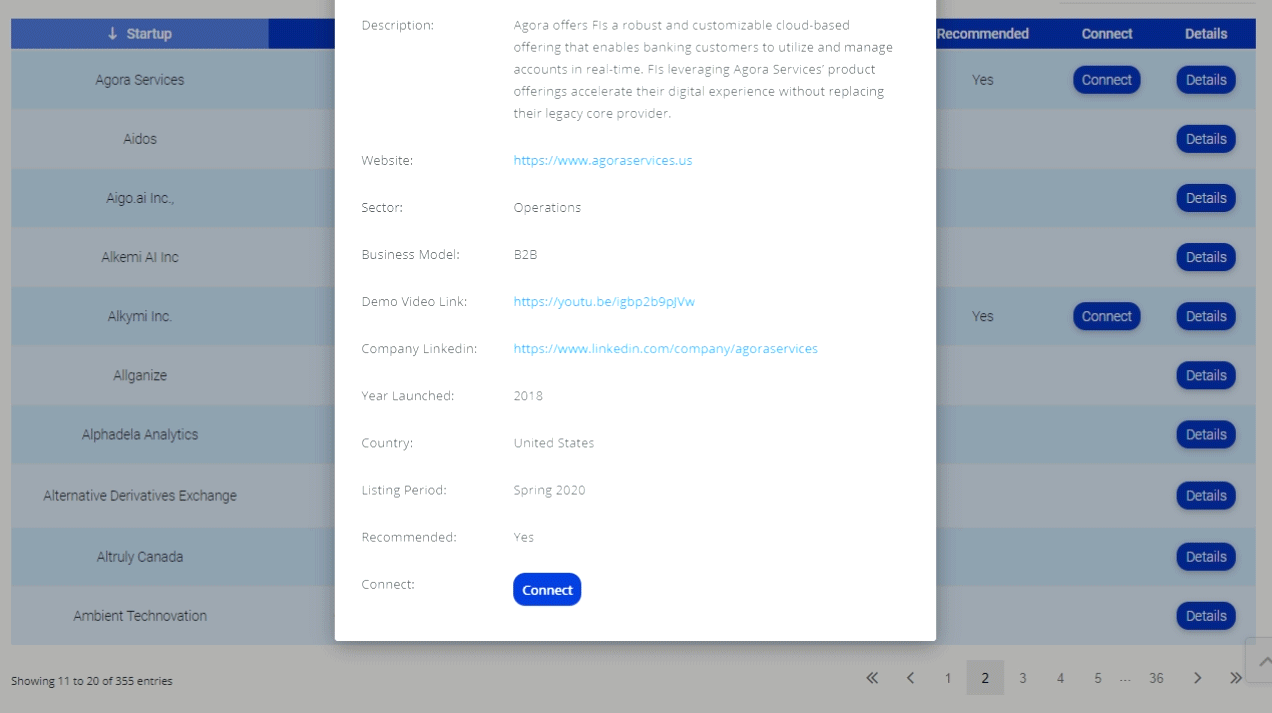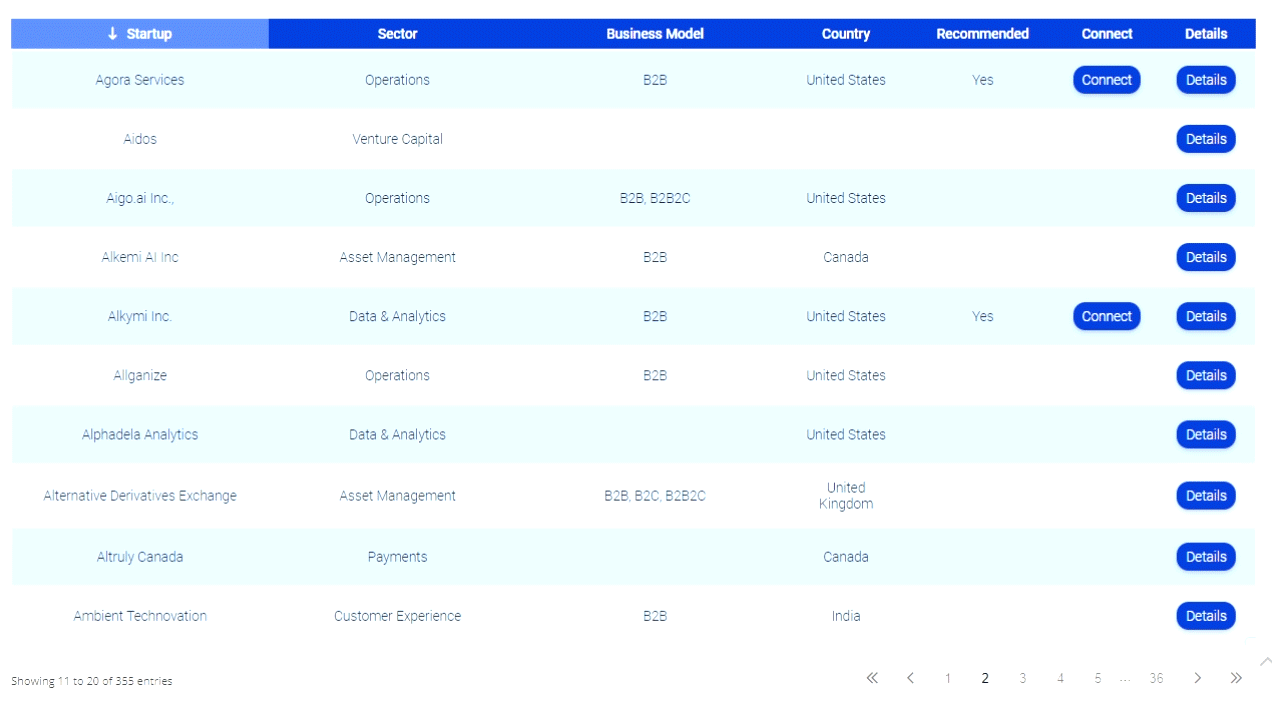
Identity Theft Expert; Are Legitimate Sites the Next Malware Threat?
Identity Theft Speaker Robert Siciliano www.IDTheftSecurity.com Excellent article here; Are Legitimate Sites the Next Malware Threat?
Lax attention to critical security patches continues to provide criminal hackers the path of least resistance inside the walls of SMBs and large enterprise networks. Most of us are privy to fundamentals such as not opening attachments, updating anti-virus, securing wireless connections, avoiding P2P downloads and not spending any time in the bowels of the web.
Where many fail is routinely updating whats is outdated or flawed. Further, attention is often paid to functionality and to build-out of an application during development than to security. Consequences often include data breach and becoming part of a botnet.
Here is a Fox News video depicting a retailer who was “compliant” but still had 300 machines infected.
Identity Theft Speaker Robert Siciliano www.IDTheftSecurity.com Excellent article here; Are Legitimate Sites the Next Malware Threat?
Lax attention to critical security patches continues to provide criminal hackers the path of least resistance inside the walls of SMBs and large enterprise networks. Most of us are privy to fundamentals such as not opening attachments, updating anti-virus, securing wireless connections, avoiding P2P downloads and not spending any time in the bowels of the web.
Where many fail is routinely updating whats is outdated or flawed. Further, attention is often paid to functionality and to build-out of an application during development than to security. Consequences often include data breach and becoming part of a botnet.
Here is a Fox News video depicting a retailer who was “compliant” but still had 300 machines infected.