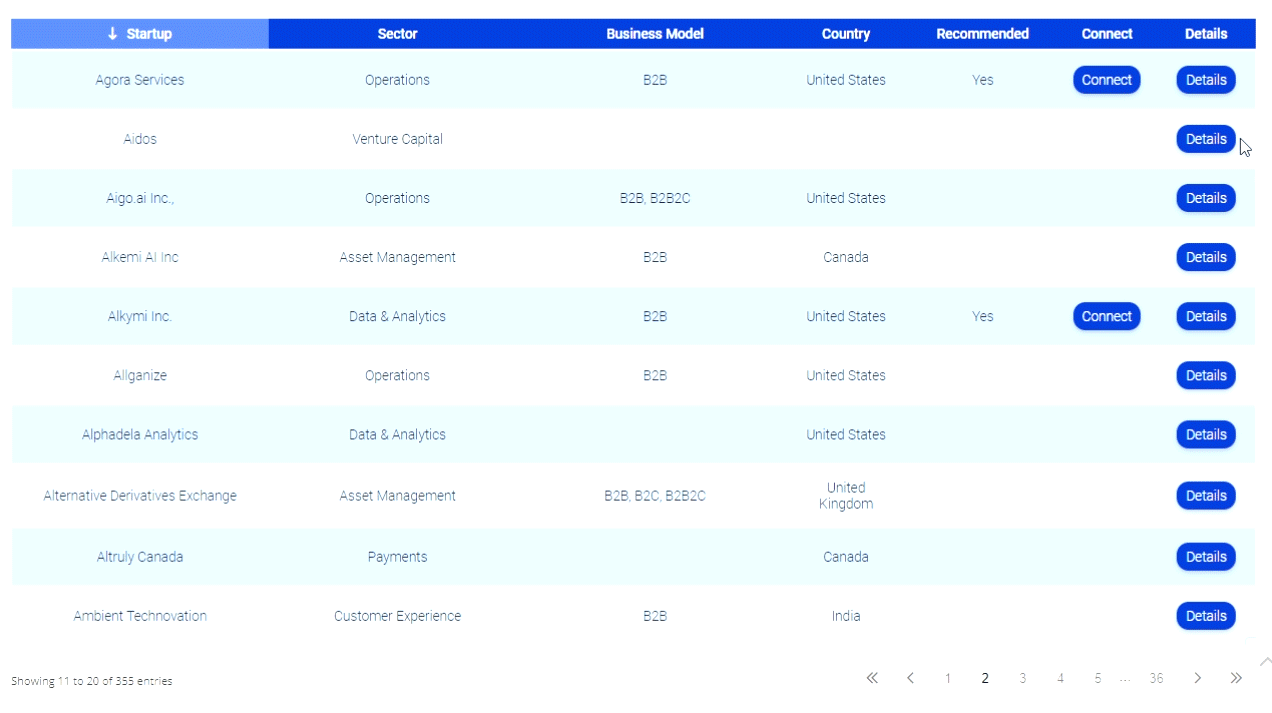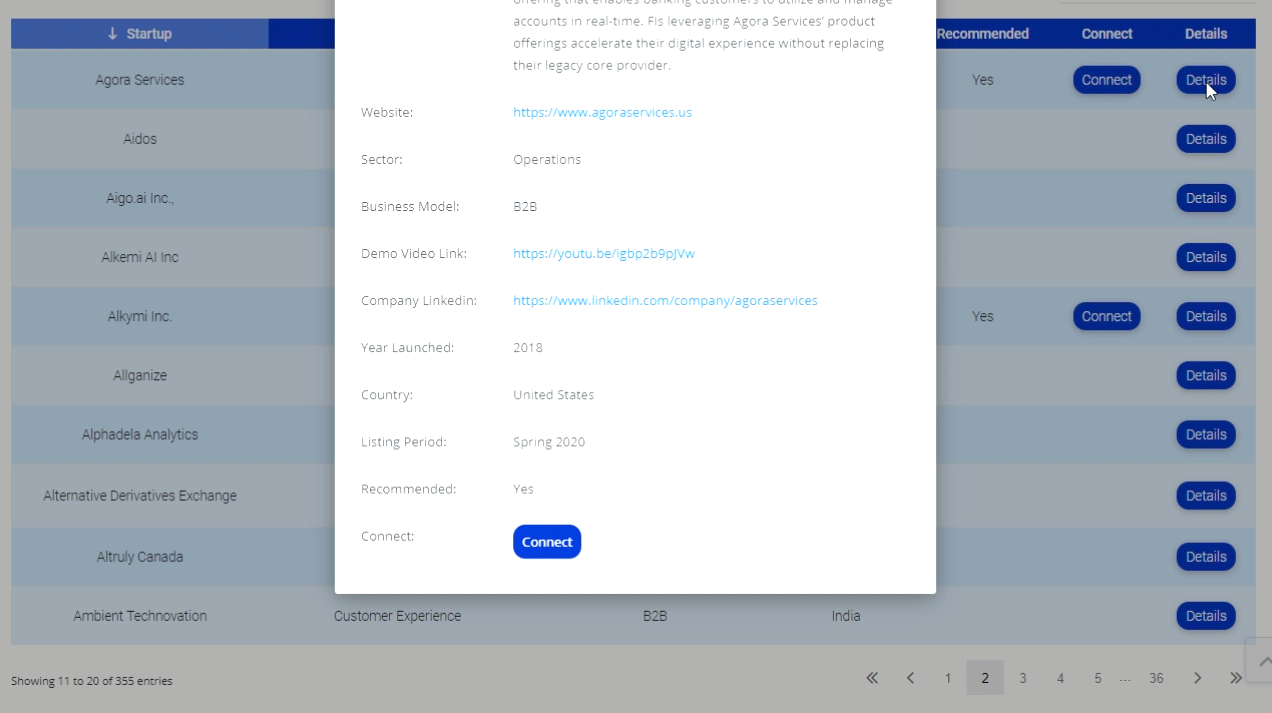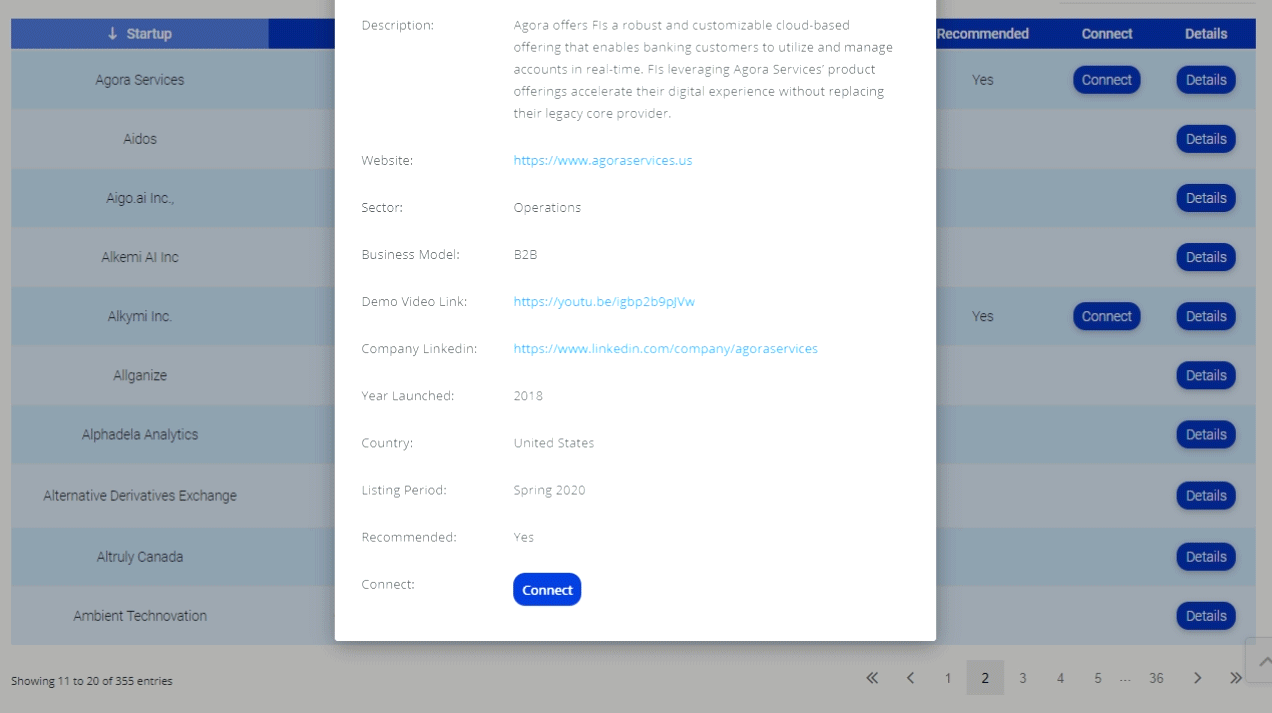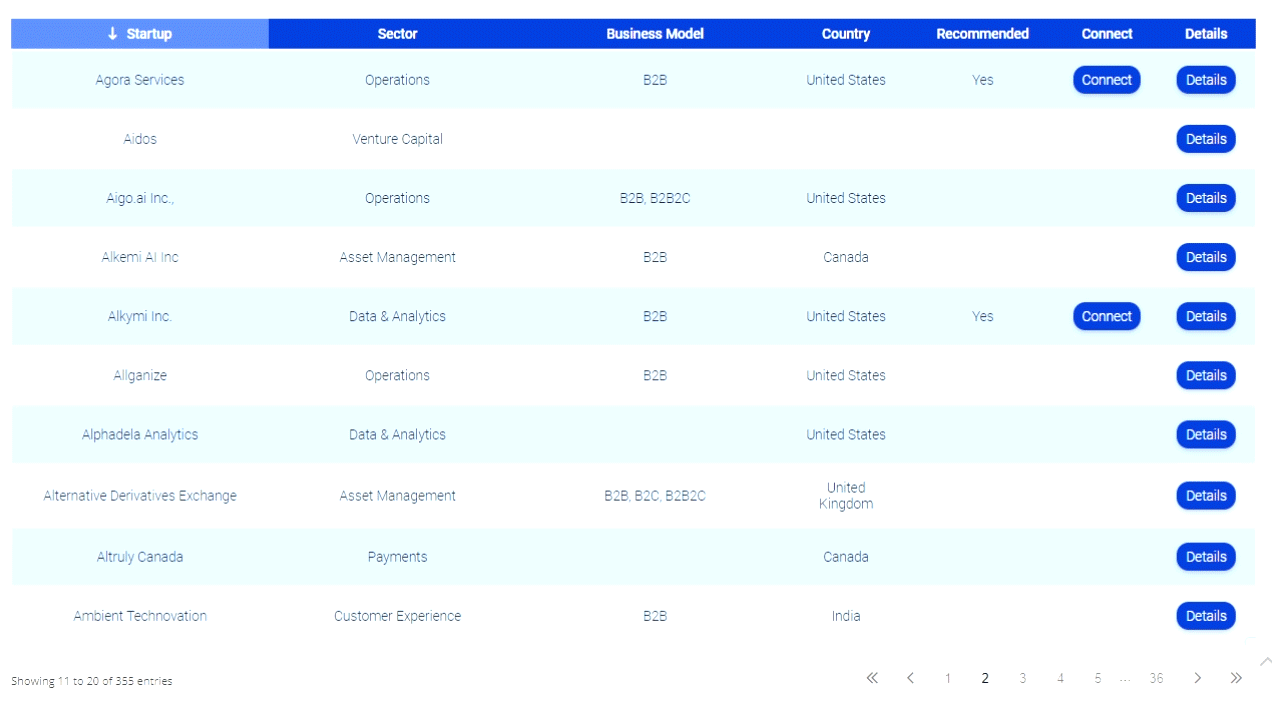
Debit card PINS hacked; Banks may need to revamp payment systems
Robert Siciliano Identity Theft Speaker
There is no end to the ingenuity of the criminal hacker. They’ve figured out how to hack debit card PINS. Debit cards are linked directly to our checking accounts, which makes them tasty treats for criminal hackers.
At an ATM or cash register, most debit card users are blissfully unaware of what occurs when they swipe their cards and enter their pin numbers. A magical mystery takes place and we get to walk away with our new purchase, simply by swiping a card and tapping a few keys. The money magically disappears from our account and we celebrate by eating the Twinkie we just bought.
Whether you’re swiping your debit card at an ATM or in a store or restaurant, the process is similar. The user swipes his or her card and types in the pin number. The data  is verified by a 3rd party payment processor or, in some cases, by a bank, over telephone lines or the Internet. Once the information has been validated and the payment processor confirms that the required funds exist, the money is moved from the user’s account to the merchant’s account, or is dispensed in cash.
is verified by a 3rd party payment processor or, in some cases, by a bank, over telephone lines or the Internet. Once the information has been validated and the payment processor confirms that the required funds exist, the money is moved from the user’s account to the merchant’s account, or is dispensed in cash.
The convenience of debit cards has led to global popularity that vastly exceeds that of handwritten checks, all the way into 3rd world countries.
We’ve known for some time that low-tech skimming at ATMs and gas pumps has been a point of compromise. Now, Wired reports that the transaction itself puts your PIN number at risk. Academics discovered this flaw years ago, but didn’t think it would be possible to execute in the field. Criminal hackers, however, have come up with the holy grail of hacks, stealing large amounts of encrypted and unencrypted debit card and pin numbers. And they have figured a way to  crack the encryption codes.
crack the encryption codes.
The first signs of PIN tampering were recognized when investigators studied the processes of the 11 criminals who were caught after the TJX data breach. That breach involved 45 million credit and debit cards. The crime ring needed PIN codes to turn that data into cash. An investigation into this breach reported that the hacks resulted in “more targeted, cutting-edge, complex, and clever cyber crime attacks than seen in previous years.”
This revelation has some saying that the only cure for this type of hack is a complete overhaul to the payment processing system.
The compromise occurs in a device called a hardware security module (HSM), which sits on bank networks. PIN numbers pass through this device on their way to the card issuer. The module is tamper-resistant and provides a secure environment for encryption and decryption for PINs and card numbers. Criminal hackers are accessing HSMs and tricking them into providing the decrypting data. They are installing malware called “memory scrapers,” which capture the unencrypted data and use the hacked system to store it.
The PCI Security Standards Council, a self regulating body that oversees much of what occurs regarding payment card transaction, said they would begin testing HSMs. Bob Russo, general manager of the global standards body, said that the council’s testing of the devices would “focus specifically on security properties that are critical to the payment system.”
I don’t own a debit card and never have and never will. Simply put, if my debit card were hacked, that money would be coming directly from my bank account. A compromised ATM or point of sale transaction often fails to exhibit evidence of hacking. This means that I’d have to go through the arduous process of convincing my bank that it wasn’t me who withdrew thousands of dollars from my account. Whereas if a credit card is compromised, the zero-liability guarantee kicks in and I’m cured much more quickly.
Your ultimate responsibility here is to check your statements very closely and look for unauthorized activity. Read your statements online biweekly as opposed to relying solely on your monthly paper statement, and refute unauthorized charges immediately. Consider using a credit card instead of a debit card.
While this type of fraud is generally out of your control it’s still imperative you invest in internet security software such as McAfee and consider identity theft protection.
Identity Theft Expert discussing flawed card transactions
I’m excited to work with uni-ball in 2009 in a partnership to help raise awareness about the growing threat of identity theft and provide tips for protecting yourself. Check out uniball-na.com for more information.
Robert Siciliano Identity Theft Speaker
There is no end to the ingenuity of the criminal hacker. They’ve figured out how to hack debit card PINS. Debit cards are linked directly to our checking accounts, which makes them tasty treats for criminal hackers.
At an ATM or cash register, most debit card users are blissfully unaware of what occurs when they swipe their cards and enter their pin numbers. A magical mystery takes place and we get to walk away with our new purchase, simply by swiping a card and tapping a few keys. The money magically disappears from our account and we celebrate by eating the Twinkie we just bought.
Whether you’re swiping your debit card at an ATM or in a store or restaurant, the process is similar. The user swipes his or her card and types in the pin number. The data  is verified by a 3rd party payment processor or, in some cases, by a bank, over telephone lines or the Internet. Once the information has been validated and the payment processor confirms that the required funds exist, the money is moved from the user’s account to the merchant’s account, or is dispensed in cash.
is verified by a 3rd party payment processor or, in some cases, by a bank, over telephone lines or the Internet. Once the information has been validated and the payment processor confirms that the required funds exist, the money is moved from the user’s account to the merchant’s account, or is dispensed in cash.
The convenience of debit cards has led to global popularity that vastly exceeds that of handwritten checks, all the way into 3rd world countries.
We’ve known for some time that low-tech skimming at ATMs and gas pumps has been a point of compromise. Now, Wired reports that the transaction itself puts your PIN number at risk. Academics discovered this flaw years ago, but didn’t think it would be possible to execute in the field. Criminal hackers, however, have come up with the holy grail of hacks, stealing large amounts of encrypted and unencrypted debit card and pin numbers. And they have figured a way to  crack the encryption codes.
crack the encryption codes.
The first signs of PIN tampering were recognized when investigators studied the processes of the 11 criminals who were caught after the TJX data breach. That breach involved 45 million credit and debit cards. The crime ring needed PIN codes to turn that data into cash. An investigation into this breach reported that the hacks resulted in “more targeted, cutting-edge, complex, and clever cyber crime attacks than seen in previous years.”
This revelation has some saying that the only cure for this type of hack is a complete overhaul to the payment processing system.
The compromise occurs in a device called a hardware security module (HSM), which sits on bank networks. PIN numbers pass through this device on their way to the card issuer. The module is tamper-resistant and provides a secure environment for encryption and decryption for PINs and card numbers. Criminal hackers are accessing HSMs and tricking them into providing the decrypting data. They are installing malware called “memory scrapers,” which capture the unencrypted data and use the hacked system to store it.
The PCI Security Standards Council, a self regulating body that oversees much of what occurs regarding payment card transaction, said they would begin testing HSMs. Bob Russo, general manager of the global standards body, said that the council’s testing of the devices would “focus specifically on security properties that are critical to the payment system.”
I don’t own a debit card and never have and never will. Simply put, if my debit card were hacked, that money would be coming directly from my bank account. A compromised ATM or point of sale transaction often fails to exhibit evidence of hacking. This means that I’d have to go through the arduous process of convincing my bank that it wasn’t me who withdrew thousands of dollars from my account. Whereas if a credit card is compromised, the zero-liability guarantee kicks in and I’m cured much more quickly.
Your ultimate responsibility here is to check your statements very closely and look for unauthorized activity. Read your statements online biweekly as opposed to relying solely on your monthly paper statement, and refute unauthorized charges immediately. Consider using a credit card instead of a debit card.
While this type of fraud is generally out of your control it’s still imperative you invest in internet security software such as McAfee and consider identity theft protection.
Identity Theft Expert discussing flawed card transactions
I’m excited to work with uni-ball in 2009 in a partnership to help raise awareness about the growing threat of identity theft and provide tips for protecting yourself. Check out uniball-na.com for more information.