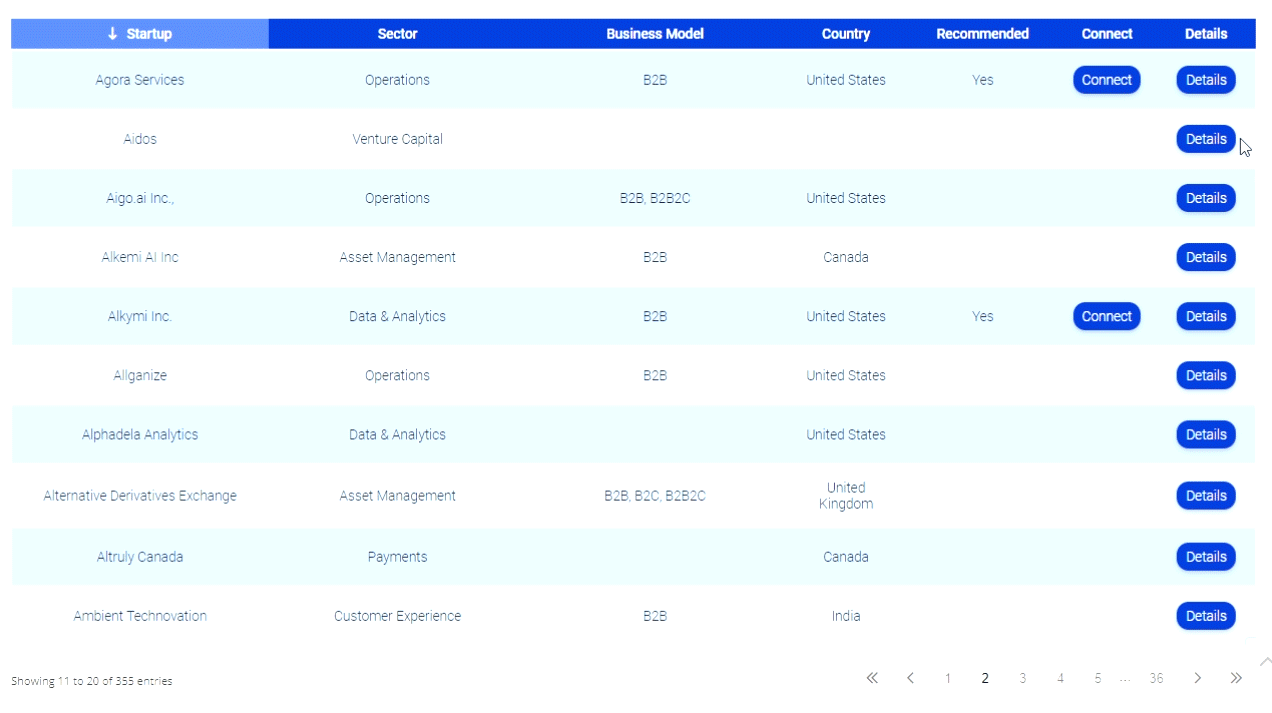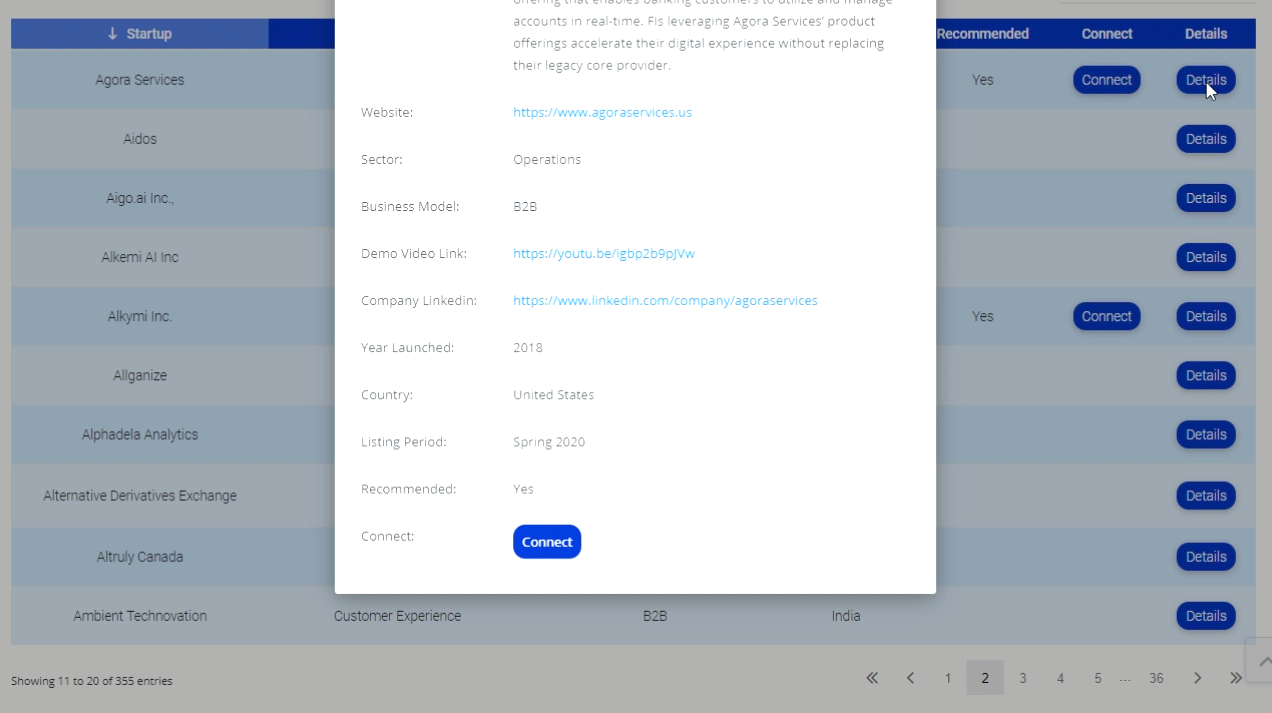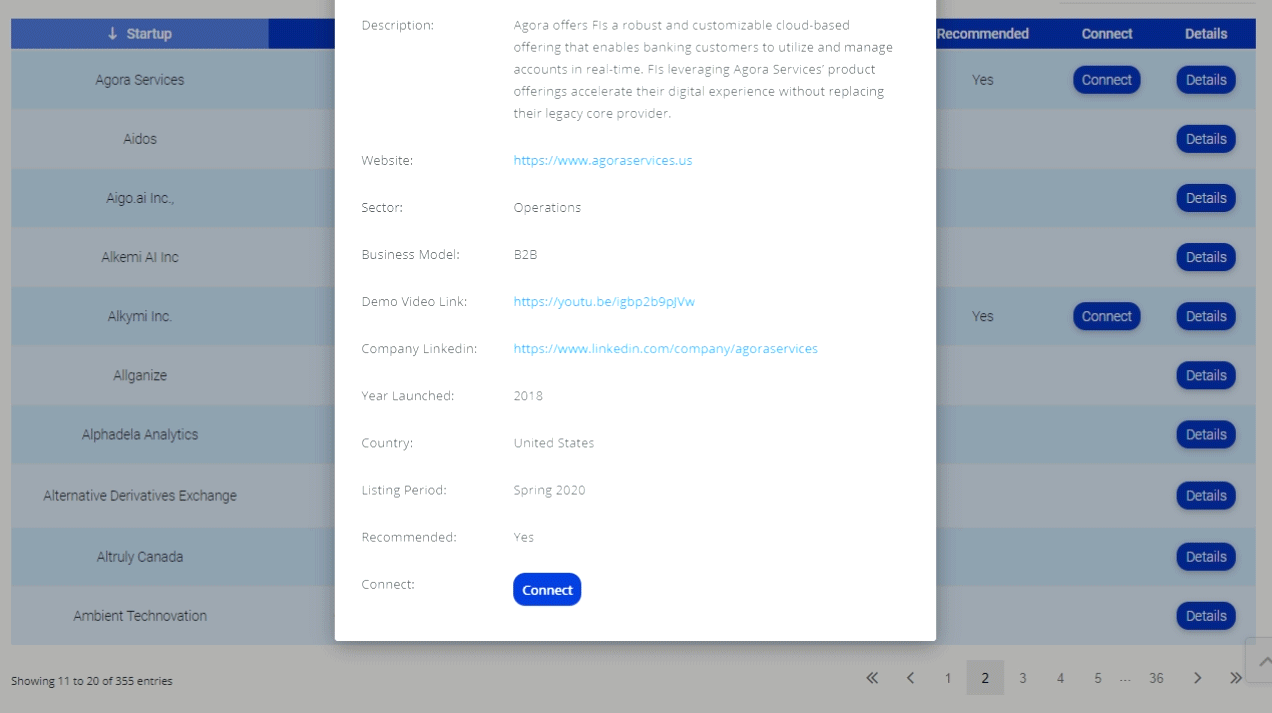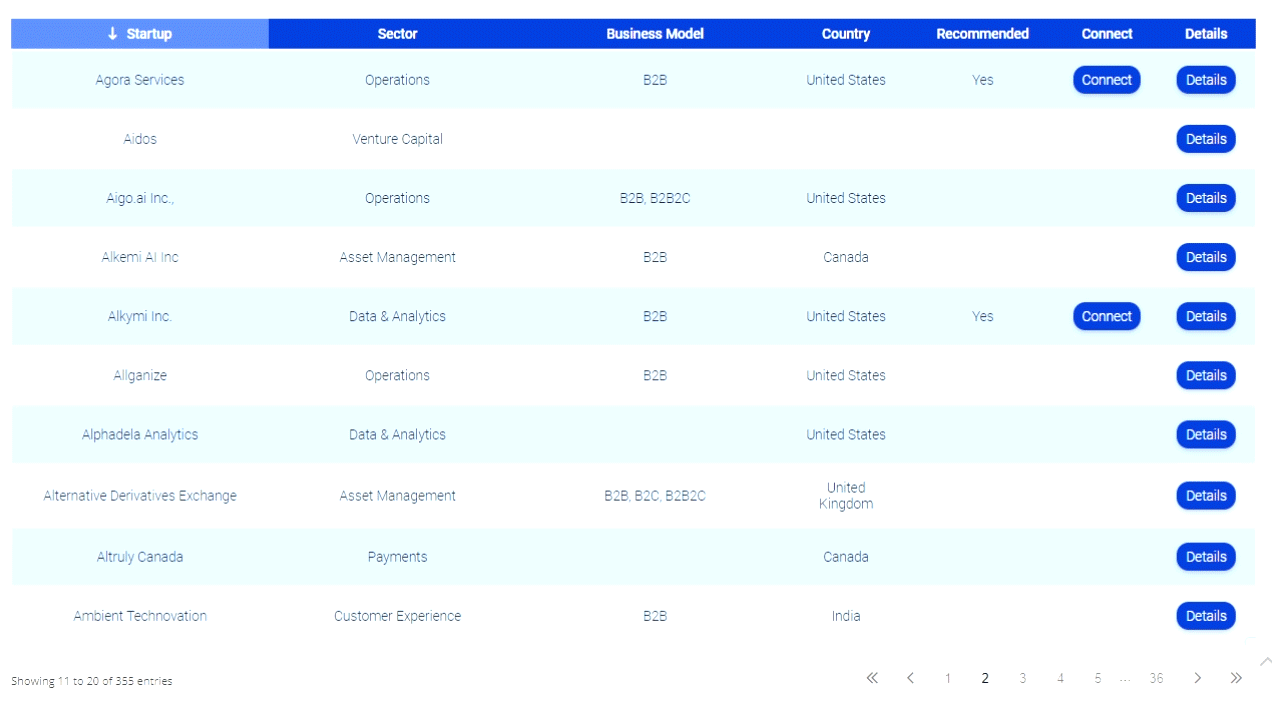
Bank manager never saw an ATM skimmer
Identity Theft Expert Robert Siciliano
Shouldn’t a banks employees know how to spot ATM skimmers? You’d think that should part of Banking Security Training 101, right? However I don’t think this is the case.
I met a charismatic gent on FOX and Friends named Sean Seibel. Sean has a unique job title at Microsoft: User Experience Evangelist. Sean’s job is to be on top of what’s new and what’s next in technology, in the next 5-7 years. He’s a futurist. He and I spoke in the green room of the show before we appeared together on a segment regarding ATM skimming.
ATM skimming often results in forms of identity theft, credit card fraud or bank fraud.
To be a User Experience Evangelist requires a certain vision, insight and the ability to go beyond what’s current or obvious. Sean proved his ability to see “more” by trumping a gang of identity thieves who set out to steal millions from ATMs but “only” got away with $500,000.
Sean stopped at an ATM to get some cash to pay his barber. When he inserted his ATM card in the machine, he noticed a bit of resistance. Most people wouldn’t think twice about this. But Sean doesn’t think like most people. Then the screen said the machine was unable to read his card so he tried again. The second time, the machine gave him an error message. Before he tried again, he thought about a report he had heard about devices that fraudsters attach to the outside of card readers on ATM machines and wondered if that was the source of his problem.
He says, “I’m looking at the thing and thinking, this can’t be. No way. There are all these stories and myths about it, but I actually found one in the wild.”
Sean was face to face with an ATM skimmer, one that he had just swiped his card through. His heart started pounding. Adrenalin was rushing through his body. He was concerned, not just that he might be scammed, but that criminals might be very close by, maybe even behind him or watching him. However, that did not deter him.
Sean says, “I tried to pull on the green plastic surrounding the card slot and found that it peeled right off.” This plastic ATM skimmer had an SD card built into it to store all the stolen data. Sean went into the bank and notified the branch manager, who had never seen an ATM skimmer and didn’t know what to do. She took the skimmer and thanked Sean.
Then Sean remembered, from numerous reports about ATM skimming, that there are usually 2 parts to the ATM skimmer. One is the skimming device itself, the second is a micro-camera placed somewhere on the machine, where it  records the user’s PIN. The camera is often installed in a false brochure holder that taped to the ATM. In this case, it was behind a small mirror that alerts the ATM user to beware of “shoulder surfers.”
records the user’s PIN. The camera is often installed in a false brochure holder that taped to the ATM. In this case, it was behind a small mirror that alerts the ATM user to beware of “shoulder surfers.”
Sean went back to the still operational ATM, where people were waiting in line for their cash, and noticed a tiny video camera behind an extra mirror attached to the machine, positioned right over the key pad where it could record user’s PINs. Not being a bank employee and not wanting to alarm any of the people iwaiting, he actually got in line, waited his turn (knowing that the skimmer was gone and nobody was in danger) and pulled the camera off the ATM.
He brought the camera to the bank manager, who replied by saying, “Maybe we should shut  that machine down, huh?” Sean said, “I think that’s a good idea.” The bank manager contacted bank security, shut down the machine and alerted other area banks. The identity thieves netted $500,000 from their scam, rather than the millions they might have stolen had Sean Seibel not foiled their operation.
that machine down, huh?” Sean said, “I think that’s a good idea.” The bank manager contacted bank security, shut down the machine and alerted other area banks. The identity thieves netted $500,000 from their scam, rather than the millions they might have stolen had Sean Seibel not foiled their operation.
Bank branch manager…ZERO
Identity Thieves……….$500,000
Sean Seibel foiling their operation and becoming a hero to many….Priceless.
Some great tips from Marite Ferrero, of CardSwitch Technology:
- Skimming has been and will continue to be the most common type of ATM-related fraud.
- Criminals attach skimming devices over card slots on ATMs to steal data as the machine reads the card’s magnetic strip.
- Hidden cameras record victims typing in their PIN codes.
- More sophisticated criminals use wireless keypad overlays, which transmit PINs to a nearby laptop, instead
 of cameras.
of cameras. - The U.S. Secret Service estimates that annual losses from ATM skimming total about $1 billion each year, or $350,000 a day.
- Bank ATMs are more vulnerable than standalone ATMs.
- Standalone ATMs in grocery stores or on the street use technology that encrypts the PIN pad, making them more difficult for criminals to hack.
- Standalone ATMs are often positioned near the watchful eye of cashiers or store owners, so it’s harder to install skimmers without being caught.
- Bank ATMs are also more highly trafficked, which means a bigger potential payoff for the criminals.
Also, invest in identity theft protection and make to update your PC’s McAfee internet security software.
Identity theft expert Robert Siciliano discusses ATM skimming.
Identity Theft Expert Robert Siciliano
Shouldn’t a banks employees know how to spot ATM skimmers? You’d think that should part of Banking Security Training 101, right? However I don’t think this is the case.
I met a charismatic gent on FOX and Friends named Sean Seibel. Sean has a unique job title at Microsoft: User Experience Evangelist. Sean’s job is to be on top of what’s new and what’s next in technology, in the next 5-7 years. He’s a futurist. He and I spoke in the green room of the show before we appeared together on a segment regarding ATM skimming.
ATM skimming often results in forms of identity theft, credit card fraud or bank fraud.
To be a User Experience Evangelist requires a certain vision, insight and the ability to go beyond what’s current or obvious. Sean proved his ability to see “more” by trumping a gang of identity thieves who set out to steal millions from ATMs but “only” got away with $500,000.
Sean stopped at an ATM to get some cash to pay his barber. When he inserted his ATM card in the machine, he noticed a bit of resistance. Most people wouldn’t think twice about this. But Sean doesn’t think like most people. Then the screen said the machine was unable to read his card so he tried again. The second time, the machine gave him an error message. Before he tried again, he thought about a report he had heard about devices that fraudsters attach to the outside of card readers on ATM machines and wondered if that was the source of his problem.
He says, “I’m looking at the thing and thinking, this can’t be. No way. There are all these stories and myths about it, but I actually found one in the wild.”
Sean was face to face with an ATM skimmer, one that he had just swiped his card through. His heart started pounding. Adrenalin was rushing through his body. He was concerned, not just that he might be scammed, but that criminals might be very close by, maybe even behind him or watching him. However, that did not deter him.
Sean says, “I tried to pull on the green plastic surrounding the card slot and found that it peeled right off.” This plastic ATM skimmer had an SD card built into it to store all the stolen data. Sean went into the bank and notified the branch manager, who had never seen an ATM skimmer and didn’t know what to do. She took the skimmer and thanked Sean.
Then Sean remembered, from numerous reports about ATM skimming, that there are usually 2 parts to the ATM skimmer. One is the skimming device itself, the second is a micro-camera placed somewhere on the machine, where it  records the user’s PIN. The camera is often installed in a false brochure holder that taped to the ATM. In this case, it was behind a small mirror that alerts the ATM user to beware of “shoulder surfers.”
records the user’s PIN. The camera is often installed in a false brochure holder that taped to the ATM. In this case, it was behind a small mirror that alerts the ATM user to beware of “shoulder surfers.”
Sean went back to the still operational ATM, where people were waiting in line for their cash, and noticed a tiny video camera behind an extra mirror attached to the machine, positioned right over the key pad where it could record user’s PINs. Not being a bank employee and not wanting to alarm any of the people iwaiting, he actually got in line, waited his turn (knowing that the skimmer was gone and nobody was in danger) and pulled the camera off the ATM.
He brought the camera to the bank manager, who replied by saying, “Maybe we should shut  that machine down, huh?” Sean said, “I think that’s a good idea.” The bank manager contacted bank security, shut down the machine and alerted other area banks. The identity thieves netted $500,000 from their scam, rather than the millions they might have stolen had Sean Seibel not foiled their operation.
that machine down, huh?” Sean said, “I think that’s a good idea.” The bank manager contacted bank security, shut down the machine and alerted other area banks. The identity thieves netted $500,000 from their scam, rather than the millions they might have stolen had Sean Seibel not foiled their operation.
Bank branch manager…ZERO
Identity Thieves……….$500,000
Sean Seibel foiling their operation and becoming a hero to many….Priceless.
Some great tips from Marite Ferrero, of CardSwitch Technology:
- Skimming has been and will continue to be the most common type of ATM-related fraud.
- Criminals attach skimming devices over card slots on ATMs to steal data as the machine reads the card’s magnetic strip.
- Hidden cameras record victims typing in their PIN codes.
- More sophisticated criminals use wireless keypad overlays, which transmit PINs to a nearby laptop, instead
 of cameras.
of cameras. - The U.S. Secret Service estimates that annual losses from ATM skimming total about $1 billion each year, or $350,000 a day.
- Bank ATMs are more vulnerable than standalone ATMs.
- Standalone ATMs in grocery stores or on the street use technology that encrypts the PIN pad, making them more difficult for criminals to hack.
- Standalone ATMs are often positioned near the watchful eye of cashiers or store owners, so it’s harder to install skimmers without being caught.
- Bank ATMs are also more highly trafficked, which means a bigger potential payoff for the criminals.
Also, invest in identity theft protection and make to update your PC’s McAfee internet security software.
Identity theft expert Robert Siciliano discusses ATM skimming.